A new cross-platform backdoor called "SysJoker" has been observed targeting machines running Windows, Linux, and macOS operating systems as part of an ongoing espionage campaign that's believed to have been initiated during the second half of 2021.
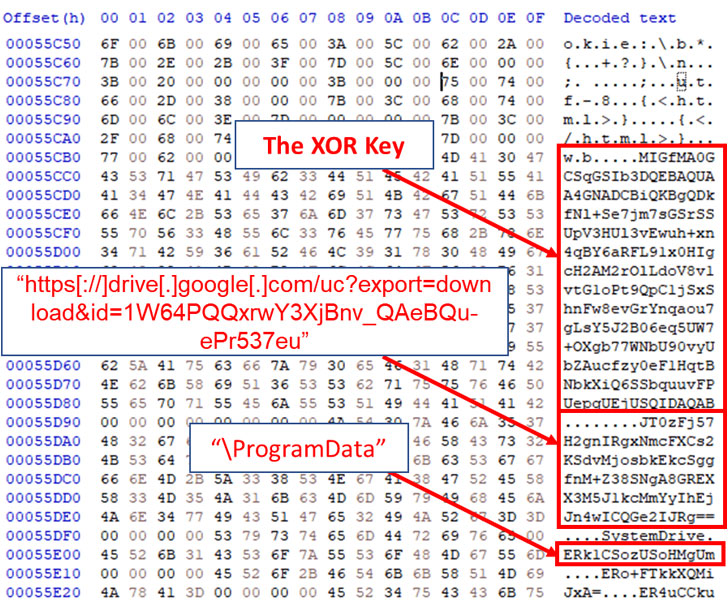
"SysJoker masquerades as a system update and generates its [command-and-control server] by decoding a string retrieved from a text file hosted on Google Drive," Intezer researchers Avigayil Mechtinger, Ryan Robinson, and Nicole Fishbein noted in a technical write-up publicizing their findings. "Based on victimology and malware's behavior, we assess that SysJoker is after specific targets."
The Israeli cybersecurity company, attributing the work to an advanced threat actor, said it first discovered evidence of the implant in December 2021 during an active attack against a Linux-based web server belonging to an unnamed educational institution.
A C++-based malware, SysJoker is delivered via a dropper file from a remote server that, upon execution, is engineered to gather information about the compromised host, such as MAC address, user name, physical media serial number, and IP address, all of which are encoded and transmitted back to the server.
What's more, connections to the attacker-controlled server are established by extracting the domain's URL from a hard-coded Google Drive link that hosts a text file ("domain.txt"), enabling the server to relay instructions to the machine that allow the malware to run arbitrary commands and executables, following which the results are beamed back.
"The fact that the code was written from scratch and hasn't been seen before in other attacks [and] we haven't witnessed a second stage or command sent from the attacker […] suggests that the attack is specific, which usually fits for an advanced actor," the researchers said.