The Israeli firm Cellebrite, which provides digital forensics tools and software to help law enforcement access mobile phones in investigations, has had its firmware and software leaked online.
Yes, you heard that right. Cellebrite's most sensitive in-house capabilities have been made public by one of its products' resellers, who is now distributing copies of Cellebrite's firmware and software for anyone to download.
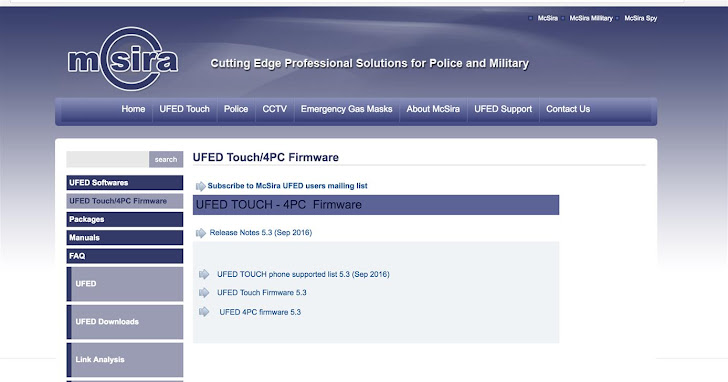
The apparent reseller is McSira Professional Solutions, which hosts software for various versions of Cellebrite's Universal Forensic Extraction Device (UFED).
UFED is one of the company's key products that help investigators bypass the security mechanisms of mobile phones, especially iPhones, and extract all data and passwords from them.
For the Cellebrite's hand on iOS devices, you can watch the 2015 YouTube video (below), which demonstrates one of the company's products that unlocked the iPhone device in few hours.
McSira is allowing anyone to download the firmware for the UFED Touch and UFED 4PC (PC version). The company is also hosting copies of UFED packages for different mobile phone brands, including Apple, Samsung, Blackberry, Nokia, and LG.
Besides this, McSira is also hosting copies of Cellebrite forensic software, such as the UFED Phone Detective, UFED Cloud Analyzer and Link Analyzer, which allows investigators to analyze seized data further.
McSira is likely offering these download links for firmware and software files so that its customers – which, according to its site, are "police, military and security agencies in the E.U. and other parts of the world" – can conveniently update their hardware to the latest version.
However, the company opened doors for researchers, hackers, and its competitors to download these leaked files, reverse-engineer them, and figure out how Cellebrite's tools break into mobile phones.
According to Joseph Cox, freelance security journalist for Motherboard, an unnamed researcher has already started examining the leaked files to disclose the kind of exploits Cellebrite uses to bypass even strong security mechanisms on mobile phones, as well as weaknesses in the implementation of affected phones that could be fixed.
Another researcher Pedro Vilaça from SentinelOne said he already cracked some of the Cellebrite software and ran it against an old iPad, though he said he needed to explore the leaked files more to understand the capability of those software better.
Mike Reilly, a PR firm representative that works with Cellebrite, said the McSira website's links "don't allow access to any of the solutions without a license key," meaning that downloaders need a key (code) given by Cellebrite or its reseller to run those software.
At the time of writing, McSira is hosting these files, but it is not clear how long the files will be hosted on its website.
McSira and Cellebrite have yet to comment on the matter.
Yes, you heard that right. Cellebrite's most sensitive in-house capabilities have been made public by one of its products' resellers, who is now distributing copies of Cellebrite's firmware and software for anyone to download.
The apparent reseller is McSira Professional Solutions, which hosts software for various versions of Cellebrite's Universal Forensic Extraction Device (UFED).
UFED is one of the company's key products that help investigators bypass the security mechanisms of mobile phones, especially iPhones, and extract all data and passwords from them.
For the Cellebrite's hand on iOS devices, you can watch the 2015 YouTube video (below), which demonstrates one of the company's products that unlocked the iPhone device in few hours.
Download Links to Cellebrite's Key Forensic Product
McSira is allowing anyone to download the firmware for the UFED Touch and UFED 4PC (PC version). The company is also hosting copies of UFED packages for different mobile phone brands, including Apple, Samsung, Blackberry, Nokia, and LG.
Besides this, McSira is also hosting copies of Cellebrite forensic software, such as the UFED Phone Detective, UFED Cloud Analyzer and Link Analyzer, which allows investigators to analyze seized data further.
McSira is likely offering these download links for firmware and software files so that its customers – which, according to its site, are "police, military and security agencies in the E.U. and other parts of the world" – can conveniently update their hardware to the latest version.
However, the company opened doors for researchers, hackers, and its competitors to download these leaked files, reverse-engineer them, and figure out how Cellebrite's tools break into mobile phones.
Researcher Started Examining leaked Software and Firmware
According to Joseph Cox, freelance security journalist for Motherboard, an unnamed researcher has already started examining the leaked files to disclose the kind of exploits Cellebrite uses to bypass even strong security mechanisms on mobile phones, as well as weaknesses in the implementation of affected phones that could be fixed.
Another researcher Pedro Vilaça from SentinelOne said he already cracked some of the Cellebrite software and ran it against an old iPad, though he said he needed to explore the leaked files more to understand the capability of those software better.
"Doesn't seem to be trying to exploit things but just data extraction," Vilaça told Motherboard. "For example, I'd to pair my device with iTunes for the logical extraction feature to work."
Mike Reilly, a PR firm representative that works with Cellebrite, said the McSira website's links "don't allow access to any of the solutions without a license key," meaning that downloaders need a key (code) given by Cellebrite or its reseller to run those software.
At the time of writing, McSira is hosting these files, but it is not clear how long the files will be hosted on its website.
McSira and Cellebrite have yet to comment on the matter.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.