Flying Under the Radar - Security Evasion Techniques
Nov 25, 2024
Threat Intelligence / Security Awareness
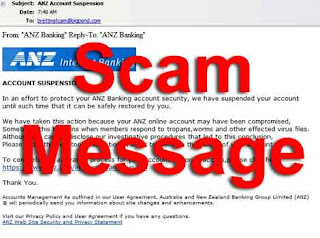
Dive into the evolution of phishing and malware evasion techniques and understand how attackers are using increasingly sophisticated methods to bypass security measures. The Evolution of Phishing Attacks "I really like the saying that 'This is out of scope' said no hacker ever. Whether it's tricks, techniques or technologies, hackers will do anything to evade detection and make sure their attack is successful," says Etay Maor, Chief Security Strategist at Cato Networks and member of Cato CTRL . Phishing attacks have transformed significantly over the years. 15-20 years ago, simple phishing sites were sufficient for capturing the crown jewels of the time - credit card details. Today, attacks and defense methods have become much more sophisticated, as we'll detail below. "This is also the time where the "cat-and-mouse" attack-defense game began," says Tal Darsan, Security Manager and member of Cato CTRL. At the time, a major defense technique against credit card phishing sites inv...