iBanking is nothing but a mobile banking Trojan app which impersonates itself as a so-called 'Security App' for Android devices and distributed through HTML injection attacks on banking sites, in order to deceive its victims.
Recently, its source code has been leaked online through an underground forum that gave the opportunities to a larger number of cyber criminals to launch attacks using this kind of ready-made mobile malware.
The malicious iBanking app installed on victims’ phone has capabilities to spy on user’s communications. The bot allows an attacker to spoof SMS, redirect calls to any pre-defined phone number, capture audio using the device's microphone and steal other confidential data like call history log and the phone book contacts.
According to new report from ESET security researchers, now this iBanking Trojan (Android/Spy.Agent.AF) is targeting Facebook users by tricking them to download a malware application.
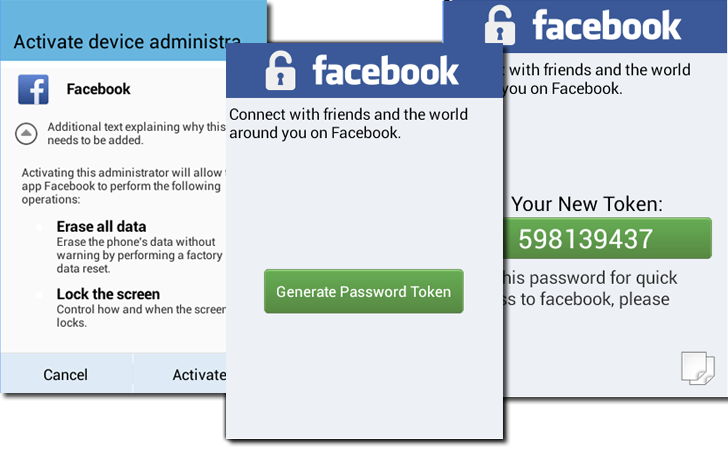
The malware uses JavaScript web injection method to create a fake Facebook Verification page for Facebook users, as shown:
Injected fake verification page prompts users to enter their mobile number in order to verify the Facebook account authenticity, and then shows the following page if he indicates that his mobile is running Android.
Next fake page asks victim to download an Android app from the shown URL or using QR code method, if SMS somehow fails to reach the user’s phone. Once downloaded and installed, the malware connects to its command-and-control server that allows attackers to issue commands to each infected device.
Facebook also has two-factor authentication features for quite a long time, but this is the very first time when Facebook users are targeted by iBanking Trojan. The reason may be an increasing number of people using it.
Since many banking sites use two-factor authentication and transaction authorization systems in order to deal with the various threats, but in order to bypass two factor authentication, cyber criminals have started to create various mobile malware like iBanking to solve their purpose.
iBanking Trojan can be used in conjunction with any malware in order to inject code into a webpage and is generally used to redirect incoming SMS messages to bypass two-factor authentication.
It is always important to treat third-party apps with a healthy dose of suspicion and skepticism as cybercriminals are always out there to hijack your every device.
Don't just download any app from any source you happen to encounter and before installing a new app, just check out the reputation of both the app and the publisher. In order to prevent direct installations, go to your Android device’s Applications Settings menu and disable the “unknown sources” option for installing apps.
Stay Safe!
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.