I am quite sure that you must be syncing your Smartphone with your Computers for transferring files and taking backup of your device.
If you are using windows operating system and Android devices, then it’s a bad news for you, because FireEye Security Researchers have identified a new piece of windows malware that can also infects your Android Devices.
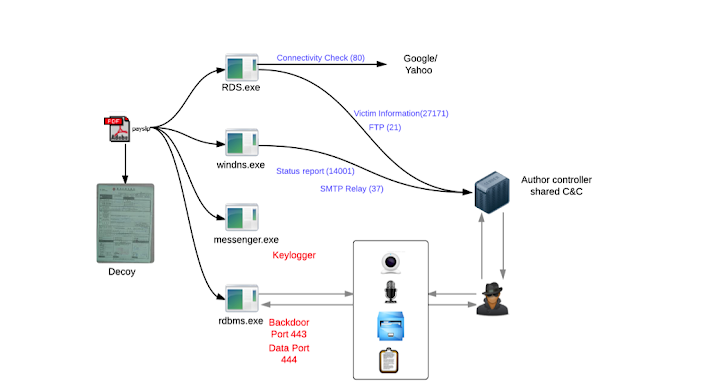
During an investigation of a targeted attack on a US based financial institution, researchers spotted a new version of Windows Remote Access Trojan (RAT) called 'Win-Spy Software Pro v16', a spying and monitoring tool. WinSpy was embedded in macro documents to kick off a spam campaign via a spear phishing email.
“The recent surge in Android-based RATs such as Dendroid and AndroRAT shows a spike in the interest of malicious actors to control mobile devices. GimmeRAT is another startling example of malicious actors venturing into the Android ecosystem,” security firm said.
The Researchers dubbed the Android spying component pre-loaded with WinSpy as GimmeRat, that allow hackers to control the victims’ device by using their own phone remotely over SMSs, or alternatively through a Windows-based controller.
"We also discovered various Android components that can be employed to engage in surveillance of a target." security firm said in a blog post.
To install the Android malware, WinSpy communicates with mobile devices connected to the infected computer using a command line tool called Android Debug Bridge (ADB), that allows the Windows malware to execute commands on the Android device. ADB is a legitimate tool and part of the official Android software development kit (SDK). If USB debugging Mode is enabled on the device, it initiates the installation process.
The new Android components also smooth the ways for surveillance of the target and there are three different applications that are part of the Android surveillance package.
“We have found three different applications that are a part of the surveillance package. One of the applications requires commandeering via a window controller and requires physical access to the device while the other two applications can be deployed in a client-server model and allow remote access through a second Android device,” wrote the researchers.
The new Android components also smooth the ways for surveillance of the target and there are three different applications that are part of the Android surveillance package.
“We have found three different applications that are a part of the surveillance package. One of the applications requires commandeering via a window controller and requires physical access to the device while the other two applications can be deployed in a client-server model and allow remote access through a second Android device,” wrote the researchers.
The technique is now new, Similar payload was used by other windows malware called ‘Trojan.Droidpak’ to infect Android Device, that was discovered by Antivirus firm Symantec in January.
Using Android malware, the attackers could trace victims’ GPS location, can take screenshots of victims’ devices and could send these data to the remote Command-and-Control servers. Trojan is also perfect in monitoring the device' text messages.
"The hostname, port, username, and password are used to connect to the attackers’ FTP server to send screenshots, which is explained, in a later section. Once this intent is received the GlobalService is restarted with the interval parameter.." FireEye said.
When Windows system infected with WinSpy, an attacker can take screenshots, log keystrokes and even can also use it to open a backdoor for remote commands, upload and download of more files and the execution of remote commands.
When Windows system infected with WinSpy, an attacker can take screenshots, log keystrokes and even can also use it to open a backdoor for remote commands, upload and download of more files and the execution of remote commands.
With the widespread use of Smartphones, the adoption of the mobile platforms such as Android has been increased, and so the new market of cyber criminals demands for RATs to support these platforms. Such interesting tactics can be used to serve fake Mobile Banking apps.. Fairly evil Ideas!
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.