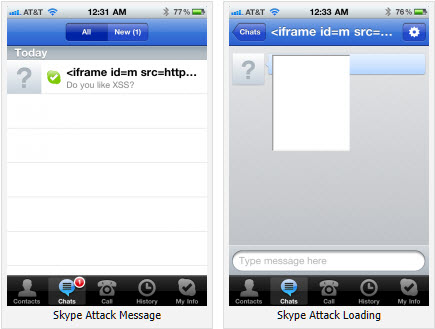
A bug in the latest version of Skype for iPhone and iPod touch makes its users vulnerable to having their address book stolen just by viewing a specially crafted message, says AppSec Consulting security researcher Phil Purviance.
The problem is made more exploitable by the way Skype uses the embeddable WebKit browser; Skype developers have set the URI scheme for the embedded browser to "file://". This error allows an attacker to access the file system and read any file that the app would be allowed to read by the iOS application sandbox. One file that every iOS application has access to is the user's SQLlite AddressBook database. In a demonstration of the bugs, Phil Purviance, AppSec Consulting security researcher, showed how it was possible to extract the iPhone address book using the vulnerabilities.
The problem is made more exploitable by the way Skype uses the embeddable WebKit browser; Skype developers have set the URI scheme for the embedded browser to "file://". This error allows an attacker to access the file system and read any file that the app would be allowed to read by the iOS application sandbox. One file that every iOS application has access to is the user's SQLlite AddressBook database. In a demonstration of the bugs, Phil Purviance, AppSec Consulting security researcher, showed how it was possible to extract the iPhone address book using the vulnerabilities.
Skype is aware of the issue and is working on a fix. “We are working hard to fix this reported issue in our next planned release, which we hope to roll out imminently,” Skype said in a statement.
Simple solution: Don't open text messages in the chat window, and check for a really quick update.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.