A threat actor operating with interests aligned with North Korea has been deploying a malicious extension on Chromium-based web browsers that's capable of stealing email content from Gmail and AOL.
Cybersecurity firm Volexity attributed the malware to an activity cluster it calls SharpTongue, which is said to share overlaps with an adversarial collective publicly referred to under the name Kimsuky.
SharpTongue has a history of singling out individuals working for organizations in the U.S., Europe, and South Korea who "work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea," researchers Paul Rascagneres and Thomas Lancaster said.
Kimsuky's use of rogue extensions in attacks is not new. In 2018, the actor was seen utilizing a Chrome plugin as part of a campaign called Stolen Pencil to infect victims and steal browser cookies and passwords.
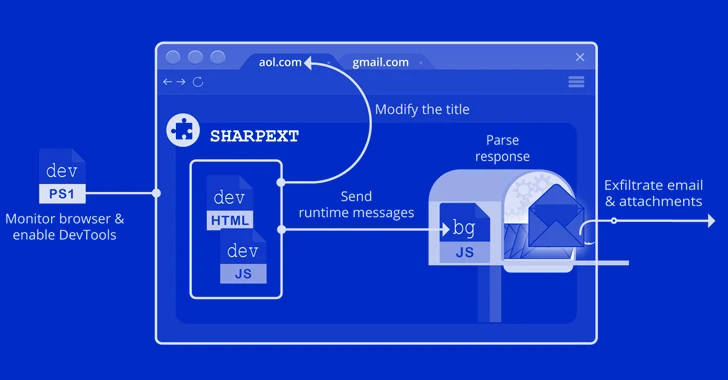
But the latest espionage effort is different in that it employs the extension, named Sharpext, to plunder email data. "The malware directly inspects and exfiltrates data from a victim's webmail account as they browse it," the researchers noted.
Targeted browsers include Google Chrome, Microsoft Edge, and Naver's Whale browsers, with the mail-theft malware designed to harvest information from Gmail and AOL sessions.
Installation of the add-on is accomplished by means of replacing the browser's Preferences and Secure Preferences files with those received from a remote server following a successful breach of a target Windows system.
This step is succeeded by enabling the DevTools panel within the active tab to steal email and attachments from a user's mailbox, while simultaneously taking steps to hide any warning messages about running developer mode extensions.
Volexity characterized the campaign as "quite successful," citing the attacker's ability to "steal thousands of emails from multiple victims through the malware's deployment."
"This is the first time Volexity has observed malicious browser extensions used as part of the post-exploitation phase of a compromise," the researchers said. "By stealing email data in the context of a user's already-logged-in session, the attack is hidden from the email provider, making detection very challenging."
The findings arrive several months after the Kimsuky actor was connected to intrusions against political institutions located in Russia and South Korea to deliver an updated version of a remote access trojan known as Konni.
Then last week, cybersecurity firm Securonix took the wraps off an ongoing set of attacks exploiting high-value targets, including the Czech Republic, Poland, and other countries, as part of a campaign codenamed STIFF#BIZON to distribute the Konni malware.
While the tactics and tools used in the intrusions point to a North Korean hacking group called APT37, evidence gathered pertaining to the attack infrastructure suggests the involvement of the Russia-aligned APT28 (aka Fancy Bear or Sofacy) actor.
"In the end, what makes this particular case interesting is the usage of Konni malware in conjunction with tradecraft similarities to APT28," the researchers said, adding it could be a case of one group masquerading as another in order to confuse attribution and escape detection.
Update: Following the publication of the story, Google told The Hacker News that the extension used in the attacks was not available on its official Chrome Web Store and that the infection requires the adversary to have already breached the target systems by other means.
"The extension in question is not in the Chrome store, and this report does not identify an exploit in Gmail," the tech giant said. "It speaks to a scenario where a system needs to already be compromised—by spear phishing or social engineering–in order for the malicious extension to be deployed."
Enabling anti-malware services and using security hardened operating systems like ChromeOS are best practices to prevent this and similar types of attacks," it further added.