Thehacker12 Dumps Logins for 20,000 Customers and U.S. Employees
Aug 24, 2011
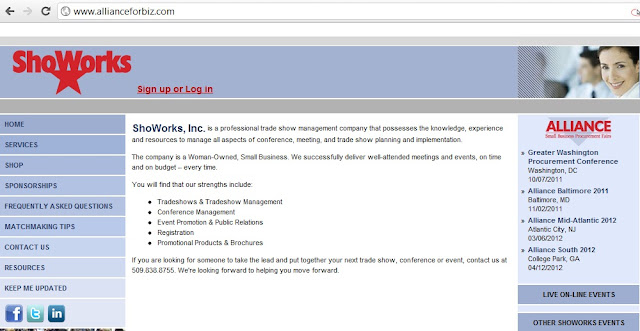
Thehacker12 Dumps Logins for 20,000 Customers and U.S. Employees ThEhAcKeR12 has hacked into an events management company and obtained sensitive information belonging to 20,000 individuals, many of whom were United States government employees or contractors. Hacker posted an Excel spreadsheet containing login credentials and personal information for 20,000 people obtained from allianceforbiz.com . Allianceforbiz.com is a professional trade show management company that manages conferences, meetings and trade shows for customers, according to the company Website. The list has been made public on Pastebin and Mediafire and a message posted on Twitter: " 20,000 email-passwords had been leaked consisting mostly of US Mill Army, Govern. & corporate giants ." The spreadsheet contains usernames, passwords, e-mail addresses. company name. The file also contained 17,668 company names, of which 14,739 were unique, and most had only one e-mail address associated with ...