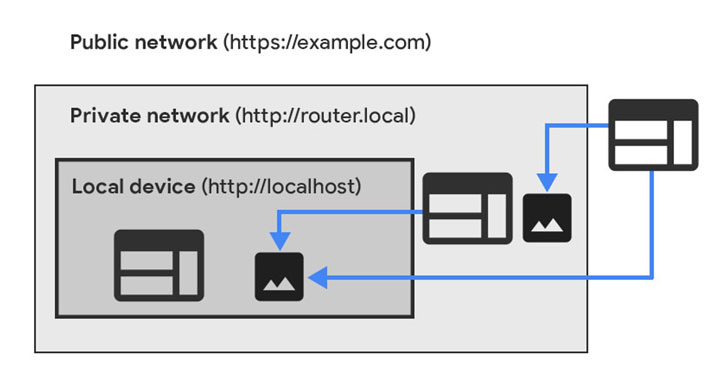
Google Chrome has announced plans to prohibit public websites from directly accessing endpoints located within private networks as part of an upcoming major security shakeup to prevent intrusions via the browser.
The proposed change is set to be rolled out in two phases consisting of releases Chrome 98 and Chrome 101 scheduled in the coming months via a newly implemented W3C specification called private network access (PNA).
"Chrome will start sending a CORS preflight request ahead of any private network request for a subresource, which asks for explicit permission from the target server," Titouan Rigoudy and Eiji Kitamura said. "This preflight request will carry a new header, Access-Control-Request-Private-Network: true, and the response to it must carry a corresponding header, Access-Control-Allow-Private-Network: true."
What this means is that starting with Chrome version 101, any website accessible via the internet will be made to seek explicit permission from the browser before they can access internal network resources. In other words, the new PNA specification adds a provision inside the browser through which websites can request servers gated behind local networks to obtain a connection.
"The specification also extends the Cross-Origin Resource Sharing (CORS) protocol so that websites now have to explicitly request a grant from servers on private networks before being allowed to send arbitrary requests," Rigoudy noted in August 2021, when Google first announced plans to deprecate access to private network endpoints from non-secure websites.
The goal, the researchers said, is to safeguard users from cross-site request forgery (CSRF) attacks targeting routers and other devices on private networks, which enable bad actors to reroute unsuspecting users to malicious domains.
It's not just Chrome. Microsoft's Chromium-based Edge browser has added a new browsing mode to the Beta channel (Version 98.0.1108.23) that aims to bring an added layer of security to mitigate future in-the-wild exploitation of unknown zero-day vulnerabilities.
"This feature is a huge step forward because it lets us mitigate unforeseen active zero days (based on historical trends)," Microsoft said. "When turned on, this feature brings Hardware-enforced Stack Protection, Arbitrary Code Guard (ACG), and Content Flow Guard (CFG) as supporting security mitigations to increase users' security on the web."