Microsoft on Thursday disclosed details of a new vulnerability that could allow an attacker to bypass security restrictions in macOS and take complete control of the device to perform arbitrary operations on the device without getting flagged by traditional security solutions.
Dubbed "Shrootless" and tracked as CVE-2021-30892, the "vulnerability lies in how Apple-signed packages with post-install scripts are installed," Microsoft 365 Defender Research Team's Jonathan Bar Or said in a technical write-up. "A malicious actor could create a specially crafted file that would hijack the installation process."
System Integrity Protection (SIP) aka "rootless" is a security feature introduced in OS X El Capitan that's designed to protect the macOS operating system by restricting a root user from executing unauthorized code or performing operations that may compromise system integrity.
Specifically, SIP allows modification of protected parts of the system — such as /System, /usr, /bin, /sbin, and /var — only by processes that are signed by Apple or those that have special entitlements to write to system files, like Apple software updates and Apple installers, while also automatically authorizing apps that are downloaded from the Mac App Store.
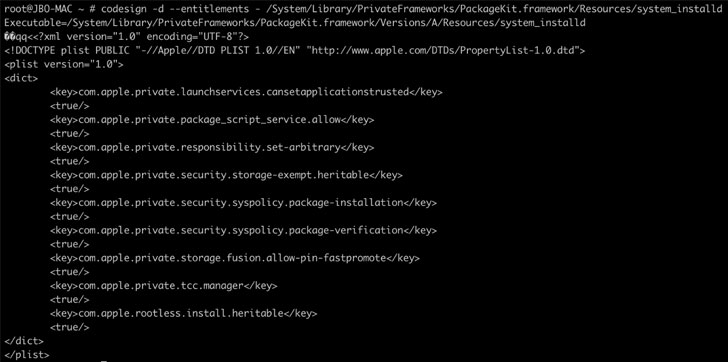
Microsoft's investigation into the security technology looked at macOS processes entitled to bypass SIP protections, leading to the discovery of a software installation daemon called "system_installd" that enables any of its child processes to completely circumvent SIP filesystem restrictions.
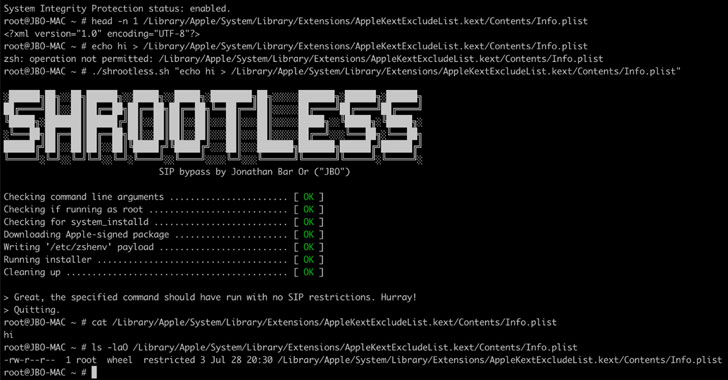
Thus when an Apple-signed package is being installed, it invokes the system_installd daemon, which, in turn, executes any post-install scripts contained in the package by invoking a default shell, which is Z shell (zsh) on macOS.
"Interestingly, when zsh starts, it looks for the file /etc/zshenv, and — if found — runs commands from that file automatically, even in non-interactive mode," Bar Or said. "Therefore, for attackers to perform arbitrary operations on the device, a fully reliable path they could take would be to create a malicious /etc/zshenv file and then wait for system_installd to invoke zsh."
Successful exploitation of CVE-2021-30892 could enable a malicious application to modify protected parts of the file system, including the capability to install malicious kernel drivers (aka rootkits), overwrite system files, or install persistent, undetectable malware. Apple said it remediated the problem with additional restrictions as part of security updates pushed on October 26, 2021.
"Security technology like SIP in macOS devices serves both as the device's built-in baseline protection and the last line of defense against malware and other cybersecurity threats," Bar Or said. "Unfortunately, malicious actors continue to find innovative ways of breaching these barriers for these very same reasons."