Many enterprises rely on more than one security tool to protect their technology assets, devices, and networks. This is particularly true for organizations that use hybrid systems or a combination of cloud and local applications. Likewise, companies whose networks include a multitude of smartphones and IoT devices are likely to deploy multiple security solutions suitable for different scenarios.
Employing several security solutions tends to be inevitable for many, especially those that have outgrown their previous network setups. Companies that expand to new branches and even overseas operations have to make use of additional security measures and tools. This use of multiple tools or software often leads to critical issues, though.
The management of the many cybersecurity solutions can become too complicated and difficult to handle, especially for organizations with little experience in addressing cyber threats, let alone actual attacks. This can result in confusion and the inability to detect vulnerabilities and respond to emerging problems properly.
The solutions
One solution to the dilemma of using different security defenses is to look for one company that provides everything to replace existing security defenses. There are security providers that offer a comprehensive range of protection, from client-based malware detection and prevention tools to SaaS security.
However, this is unlikely to be a convenient choice for most organizations. Switching to a new cybersecurity solution provider entails a major change and is possibly going to be more costly with everything taken into account. It also does not always guarantee better protection.
The second solution does not require a switch to a different platform or security provider. It is all about centralizing and unifying even fragmented sets of security solutions. Organizations can use a solution that serves as a cybersecurity central command platform to monitor and manage all security tools through a unified dashboard.
Centralized cybersecurity
To exemplify the idea of centralized cybersecurity Cyrebro has designed a security solution that unifies all of the security tools of an organization to make it easier to track security events, proactively deal with cyber threat intelligence, and ensure a rapid incident response.
Cyrebro touts three highlight features: centralized vision, a single cyber brain, and transparent accountability.
Centralized vision refers to Cyrebro’s ability to get information on all security events and have a clear sense of what they mean to the organization. It is not only about gathering details from various sources. It is also about making sense out of all the data through correlation and other approaches that take advantage of having unified access to data from various sources. It also enables smart prioritization when it comes to addressing threats.
Meanwhile, Cyrebro’s “single cyber brain” utilizes proprietary detection algorithms to track, analyze, and interpret the possible outcomes of security events as detected by the different security solutions employed by an organization. It works on the idea of turning chaos into clarity made possible through automatic integration, instant contextual analysis, and easy-to-understand real-time recommendations.
Additionally, Cyrebro helps ensure transparent accountability, which means that the centralization does not only result in the streamlining of security controls. Another vital goal of Cyrebro is to inform organizations which solutions work and which require tweaking, reconfiguration, or in some cases, complete replacement. It provides a clearer perspective of how secure or not an organization is with its current set of measures.
One important feature worth mentioning about Cyrebro is that it is technology-agnostic. It does not matter what kind of security solutions are used in an organization or which specific platforms or operating systems they are built to work with. To ensure effective cybersecurity unification and centralization, Cyrebro cannot discriminate which antivirus, firewall, or other security software tool it can work with. It has to be compatible with virtually all solutions to achieve comprehensive visibility and effective security management.
Simplified process
So how exactly does cybersecurity unification and centralization work? It’s simpler than what many would probably expect. Going back to Cyrebro as the example, the process takes only a few steps.
Cyrebro is a SaaS solution, so it does not require any software installation or maintenance. The first step is simply to obtain a username and password to be able to log in to the system and access its resources.
After logging in, the integration of security solutions follows. Basically, this means connecting all of an organization’s security tools to Cyrebro, so they can be monitored and managed. Cyrebro works with various antiviruses, endpoint detection and response software, security information and event management applications, network firewalls, web application firewalls, secure web gateways, VPNs, email security tools, cloud access security brokers (CASB), IDS/IPS security tools, cloud platforms, data loss prevention systems (DLS), network access controls (NACs), privileged access management (PAMs), and user and entity behavior analytics (UEBA) solutions.
 |
| Screenshot of the Cyrebro dashboard |
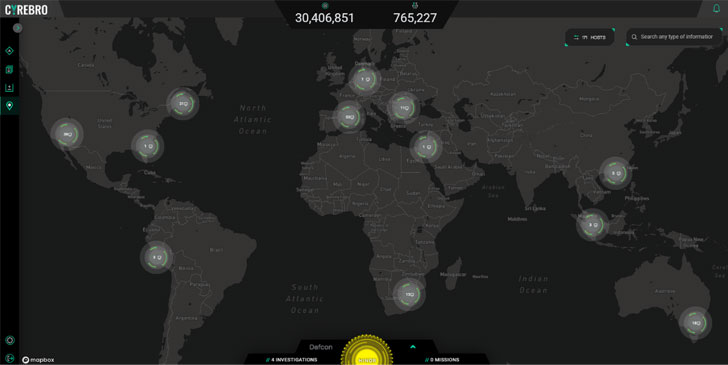
After integration is completed, organizations can start monitoring all security activities as information from various points converge in a single Cyrebro dashboard. Everything the security officers need to know is shown in a unified and centralized interface with contextual details to facilitate a better understanding of the security events detected.
Benefits of centralization
By having comprehensive visibility of the entire enterprise cybersecurity system, CTOs, CISOs, as well as CIOs have a better understanding of their security stance. They are not left in the dark because of unnecessary red tape or the incompetence of those tasked to manage specific security solutions in specific branches or offices.
This infers proactive security defense wherein organizations know what matters for their network protection and what to do when they encounter threats and attacks. Centralization enables strategic monitoring as a unified cybersecurity platform like Cyrebro is designed to provide contextual visibility across systems, making it faster and easier to detect the early signs of suspicious network activity.
Strategic monitoring, in turn, results in enhanced threat intelligence and snappier incident response. Cyrebro has a continuous Indication of Compromise (IOC) feature based on granular contextual details and machine learning to make sure that all the right alerts are raised in a timely manner. It is easy to generate security alerts, but too many of them can stifle response as it would be difficult to go through thousands of security incidents. Proper threat intelligence requires efficiency, which means the need to minimize false positives without reducing the thoroughness of threat detection and contextual analysis.
According to a CNBC report, 93 percent of attacks manage to compromise assets within a few minutes. Similarly alarming, the global average for cyber attack dwell time is 146 days according to a report cited by Infocyte. This means that it takes organizations nearly five months to detect attacks from the time the compromise happened.
Organizations need to be quick in responding to attacks, something that can only be done by promptly knowing all of the vital security incident details. Quick response and mitigation lessen the impact of security incidents on business continuity. Cyrebro improves this quick response benefit further by including real-time security analyst support to help organizations with minimal cybersecurity experiences assess their information better.
Additionally, cybersecurity centralization enables system optimization based on all the threat intelligence and updates accumulated. It also promotes proactive threat hunting, to make sure that nothing penetrates the security defenses and sleeper attacks are detected before they get activated.
 |
| Screenshot of the Cyrebro threat information search interface |
Moreover, the unification of enterprise security solutions provides a significant boost to forensic investigations. With all security data compiled in one place for easy access, organizations can accelerate ongoing investigations over suspected incursions. Also, in cases when highly sophisticated attacks manage to penetrate, especially insider-driven ones, centralization makes it easy to scrutinize everything to determine what went wrong and plug the vulnerabilities or change ineffective measures.
 |
| Screenshot of the Cyrebro Investigations interface |
Who needs cybersecurity centralization?
Cyrebro is designed for a wide variety of users, from micro and SMBs to enterprises and managed security service providers. Logically, if an organization uses many security solutions, it would be better to unify them for easier monitoring and response. Regardless of the size, a business can be prone to frequent attacks and vulnerabilities because of the use of various devices and multiple networks and web services.
Cyrebro recently received a report from a client about a phishing scheme. The website of a humanitarian aid agency was used by a malicious actor who sent emails that resembled a legitimate service notification from Microsoft.
The phishing URL reportedly redirects multiple times, ultimately landing on a simulated Microsoft login page. Clueless victims who enter their login details end up submitting their credentials through POST to the same phishing domain. The humanitarian aid agency apparently suffers from a reflected XSS or cross-site scripting vulnerability, and they had no prior knowledge of this until Cyrebro informed them.
This case is a demonstration of how everyone needs to pay extra attention to their security posture. Small businesses or large enterprises need to have a proactive and high-visibility cybersecurity policy to make sure that all hints of a possible social engineering scheme are detected and addressed promptly. At the same time, larger organizations or institutions should also ensure extensive security visibility not only to deter attacks against them but also to avoid becoming an unwitting accomplice in phishing or other sophisticated cyber attacks.
Without cybersecurity centralization, Cyrebro’s client would not have promptly detected the phishing attack. Meanwhile, if the humanitarian aid agency had a centralized cybersecurity posture, they would have detected the vulnerability in their website and implemented the necessary remedies.
The takeaway
Centralization may be frowned upon in the capitalist world, but it tends to be the more preferable approach when it comes to security. There’s a reason why in decentralized federal forms of government, the defense role is assigned to the federal government, and states are not left to handle defense and security concerns individually.
At the height of the hacktivism attacks against the United States government, a Boston University paper called for cybersecurity centralization to improve response to the ongoing threats. Centralization allows security professionals to coordinate better and evaluate vulnerabilities, threats, and actual attacks with greater accuracy and efficiency.
Effective defense posture necessitates coordination, collaboration, and comprehensive visibility. Competition among departments, branches, or units rarely results in anything productive. It only creates siloing, which prevents the sharing of useful information and technologies that could bolster defenses and enable prompt response to threats and attacks.




























