Two weeks ago, we reported how a serious flaw in the popular peer-to-peer BitTorrent file sharing protocols could be exploited to carry out a devastating distributed denial of service (DDoS) attack, allowing lone hackers with limited resources to take down large websites.
Good news is that the developers of BitTorrent have fixed the security issue in its service that is being used by hundreds of Millions of users worldwide.
In a blog post published Thursday, BitTorrent announced that the flaw was resided in a reference implementation of the Micro Transport Protocol (uTP) called libuTP, which is used by many widely used BitTorrent clients such as μTorrent, Vuze and Mainline.
The San Francisco company also announced that it has rolled out a patch for its libuTP software that will stop miscreants from abusing the p2p protocol to conduct Distributed Reflective Denial-of-Service (DRDoS) attacks.
DRDoS attack is a more sophisticated form of conventional DDoS attack where open and misconfigured DNS (Domain Name System) can be used by anyone to launch high-bandwidth DDoS attacks on the target websites.
The vulnerability was made public two weeks ago by a research team led by Florian Adamsky of the City University London.
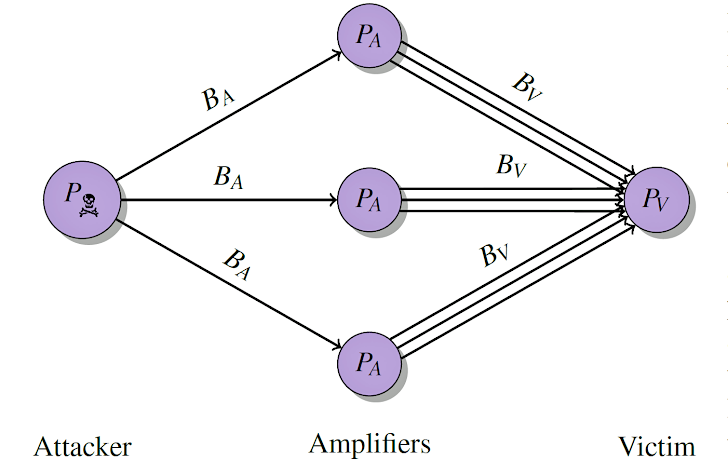
The researcher showed how an attacker could send malicious data to vulnerable BitTorrent applications to flood a third-party target with data traffic of up to a factor of 120 times bigger than the original request.
Just by replacing the attacker's IP address in the malicious User Datagram Protocol (UDP) packet with the spoofed IP address of the target, a hacker could flood the target server with data traffic, effectively making it offline.
However, BitTorrent said the company has yet not seen such attacks actively exploited in the wild.
"Florian responsibly contacted [BitTorrent] to share his findings," Christian Averill from BitTorrent wrote in a blog post. "This gave our engineering team the opportunity to mitigate the possibility of such an attack."
According to the company, uTorrent, BitTorrent and BitTorrent Sync clients were all patched up earlier this month.
However, to fix the issue, the BitTorrent and uTorrent clients will require acknowledgment packets from connection initiators before providing responses.
Denial of Service Amplification attacks are not at all new. The DoS amplification attacks have increased in the past years, and miscreants are mostly taking its advantages to attack major sites.
Last year, we saw cyber criminals exploiting a security weakness in the home and small office routers in order to amplify the bandwidth of their attack.
Also the same year, hackers succeeded in touching new heights of the massive DDoS attack targeting anti-DDoS protection firm CloudFlare with a massive 400Gbps DDoS attack.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.