A security researcher has discovered an easy way to infect Apple’s Macintosh computers with an unusual kind of malware using its own Thunderbolt port.
The hack was presented by programming expert Trammell Hudson at the annual Chaos Computer Congress (30C3) in Hamburg Germany. He demonstrated that it is possible to rewrite the firmware of an Intel Thunderbolt Mac.
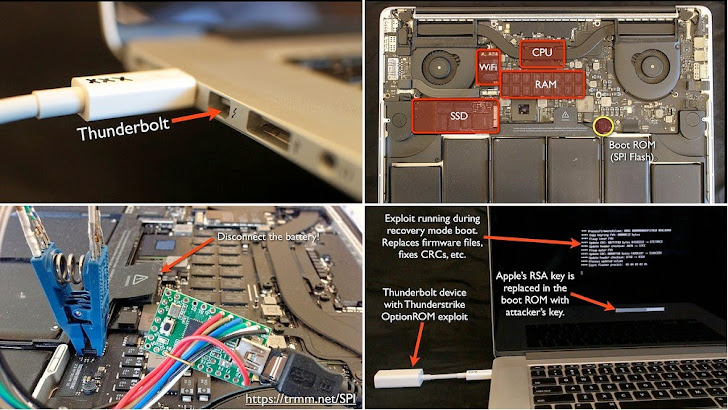
The hack, dubbed Thunderstrike, actually takes advantage of a years-old vulnerability in the Thunderbolt Option ROM that was first disclosed in 2012 but is yet to be patched. Thunderstrike can infect the Apple Extensible Firmware Interface (EFI) by allocating a malicious code into the boot ROM of an Apple computer through infected Thunderbolt devices.
The hack is really dangerous as, according to the researcher, there is no means for the user to detect the hack, or remove it even by re-installation of the complete OS X, only because the malicious code actually is in the system’s own separate ROM.
"Since the boot ROM is independent of the operating system, reinstallation of OS X will not remove it. Nor does it depend on anything stored on the disk, so replacing the hard drive has no effect. A hardware in-system-programming device is the only way to restore the stock firmware."
Hudson also showed that he could replace Apple's own cryptographic key with a new one, which will prevent legitimate firmware updates from being accepted.
"There are neither hardware nor software cryptographic checks at boot time of firmware validity, so once the malicious code has been flashed to the ROM, it controls the system from the very first instruction," Trammell Hudson said. "It could use SMM and other techniques to hide from attempts to detect it."
In addition to writing a custom code to the boot ROM, Hudson’s presentation also notes a method by which the bootkit could replicate itself to any attached Thunderbolt device, giving it the ability to spread across even air-gapped networks.
In short, an attacker could use the vulnerable Thunderbolt port to install a custom bootkit, which could even replicate itself to any other Thunderbolt-attached device, thereby spreading all over across the networks.
You can watch the entire presentation given by Hudson below and can also refer this blog post to know more about Thunderstrike.
As far as Hudson knows, there are no Mac firmware bootkits in the wild and at this time, it exists only as a proof-of-concept. So, we can presume that the vulnerability can only be exploited if the attacker has physical access to the Thunderbolt Mac. Therefore, a regular Mac user need not to worry about the hack.
Apple has already patched part of the vulnerability in the latest Mac mini and on the iMac with 5K Retina Display, which will soon be available for other Macs.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.