Traffic Interception Vulnerability found in Cyberoam
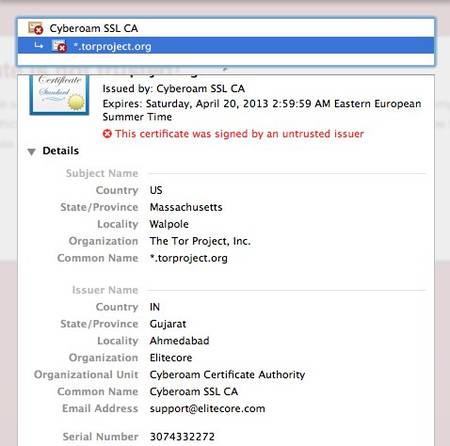
The TOR team have discovered a fake certificate in the wild. The certificate, issued by a US company called Cyberoam, was used in an attempt to trick a user in Jordan into believing that her/his connection to the TOR website, was private and secure, though in fact it was being spied upon by a Cyberoam device.
This issue was discovered and analysed by Runa A. Sandvik of the TorProject and Ben Laurie. A certificate handling flaw in Cyberoam’s deep packet inspection (DPI) devices allow traffic from a single ‘victim’ to be intercepted by any DPI device from the vendor, according to the Tor Project.
Cyberoam make a range of DPI devices which are capable of intercepting SSL connections. “While investigating this further, Ben Laurie and I found a security vulnerability affecting all Cyberoam DPI devices. Examination of a certificate chain generated by a Cyberoam DPI device shows that all such devices share the same CA certificate and hence the same private key,” Runa A. Sandvik, security researcher at Tor Project, explained.
Because the devices all use the same CA certificate, anyone in the possession of one of these devices can intercept traffic from any user accessing the network through a different Cyberoam device. Since all of the devices also include the same private key, this key can be extracted and imported into other DPI systems as well, enabling that same traffic to be intercepted.
Tor Browser Bundle are not impacted, but other users should check to ensure that the certificate in question is not installed in their web browser. Victims should uninstall the Cyberoam CA certificate from theirbrowsers and decline to complete any connection which gives acertificate warning.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.