With SaaS applications now making up the vast majority of technology used by employees in most organizations, tasks related to identity governance need to happen across a myriad of individual SaaS apps. This presents a huge challenge for centralized IT teams who are ultimately held responsible for managing and securing app access, but can’t possibly become experts in the nuances of the native security settings and access controls for hundreds (or thousands) of apps. And, even if they could, the sheer volume of tasks would easily bury them.
Modern IT teams need a way to orchestrate and govern SaaS identity governance by engaging the application owners in the business who are most familiar with how the tool is used, and who needs what type of access.
Nudge Security is a SaaS security and governance solution that can help you do just that, with automated workflows to save time and make the process manageable at scale. Read on to learn how it works.
1 . Discover all SaaS apps used by anyone in the org
As the old saying goes, you can’t secure what you can’t see, so the first step in SaaS identity governance is to get a full inventory of what technology is actually being used, and by whom.
Nudge Security discovers and categorizes all SaaS apps ever introduced by anyone in the organization and provides a vendor security profile for each app to give IT and security teams the context they need to vet new SaaS providers. And after they’ve reviewed an app, they can assign a status like “Approved,” “Acceptable,” or “Unacceptable” to indicate if usage should be permitted. For any apps that are deemed “Unacceptable”, automated nudges can be triggered in response to new accounts to redirect the user towards a similar, approved app or ask for context on why they need to use that particular app.
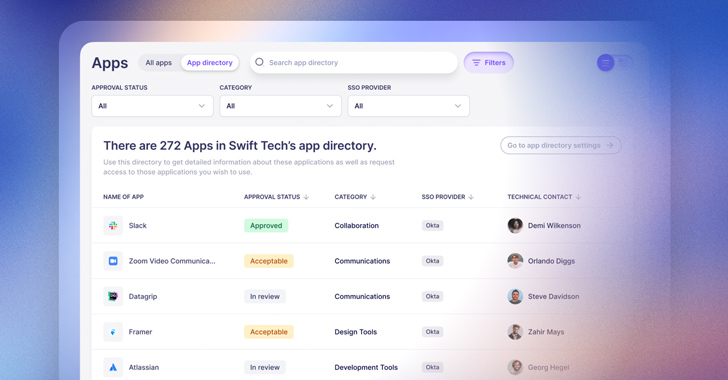
2. Share a directory of approved apps with employees
In an ideal world, IT teams want to empower employees to adopt technologies that will both enhance productivity and keep the business secure and compliant. Unfortunately, employees often have no way of knowing which tools fit the business’s requirements as well as their own.
Nudge Security makes it easy to create and share an app directory with employees, so everyone in the org can view a comprehensive list of approved applications that meet appropriate security and compliance standards. Employees can peruse the list by category and submit access requests that are routed directly to each application’s technical owner, whether or not that person sits within central IT. This removes the need for IT to be the “event forwarder” between users and app owners, while still retaining visibility and centralized governance.
3. Keep app owners up to date
Ever feel like you’re on the world’s worst scavenger hunt when tracking down the right people in your organization to get context on a SaaS application or user account? You’re not alone. This knowledge is often siloed and changes frequently. Nudge Security uses various methods to deduce the likely “technical contact” (like the first user) for every SaaS application discovered in your environment and gives you the ability to automate nudges to confirm app ownership periodically.
With this technical contact discovery process, Nudge Security automates emails or Slack messages to assumed technical contacts with a simple nudge that asks them to either validate that they are the correct technical contact or update this information. No more strings of emails and Slack threads to figure it out. With Nudge Security, you can automate the process of keeping this information up to date as administrative responsibilities change.
4. Automate user access reviews
For companies subject to any of a number of compliance standards like SOC 2, HIPAA, PCI DSS, and others, it is typically required to do periodic user access reviews of in-scope systems to ensure that only those who need access actually have access. And, for anyone who’s had the pleasure of conducting user access reviews, you know it usually involves an assortment of spreadsheets with inconsistent and incomplete information and a lot of manual effort to track down who’s using what.
Instead of this spreadsheet puzzle, with Nudge Security you can automate the process. First, you can group your in-scope assets together and automate nudges to app users to verify if they still need access. Then, Nudge Security collects the responses for you and routes the consolidated list of accounts to be removed to the app owners. Finally, it collects responses from the app owners to confirm they’ve completed the removals and documents all the actions taken in a .pdf report you can share with auditors.
5. Identify and clean up unused accounts
Meeting compliance requirements is one good reason to regularly review who needs access to what, but cost savings is another. Gartner's research shows that 25% of SaaS is underutilized or over-deployed. No matter what the size of your organization, that can add up quickly.
Nudge Security monitors cloud and SaaS account status across your entire organization, so you can easily find and prune inactive and abandoned SaaS accounts. And, you’ll have up-to-date information at your fingertips in some very good-looking charts, so you can monitor SaaS account statuses right next to SaaS adoption trends.
While you can always discover unused accounts one app at a time from each application’s overview page, Nudge Security’s playbook for removing unused accounts enables you to audit multiple applications at once so you reduce SaaS sprawl at scale.
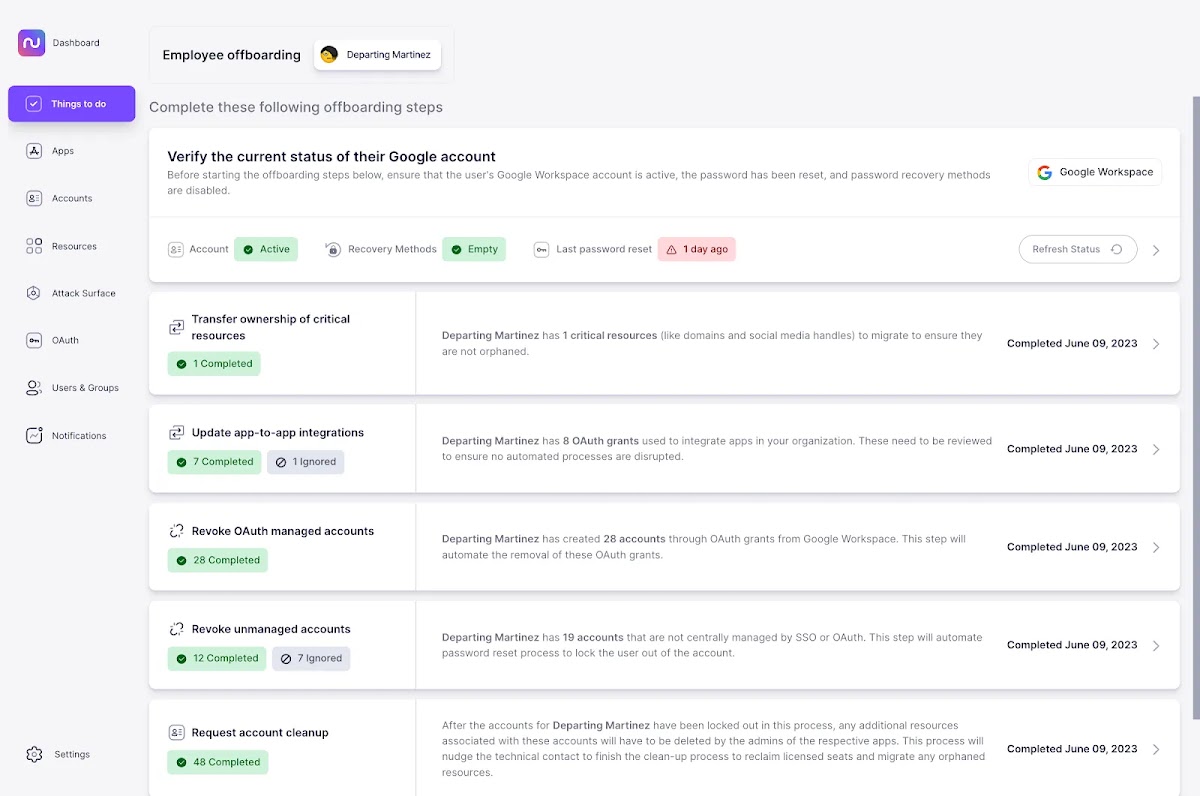
6. Ensure complete offboarding
Here’s a dirty little secret: most employees have signed up for apps outside the purview of IT, or even their department managers. With Nudge Security, you can see every account ever signed up for by anyone using an email associated with your organization. This includes domain registrations, social media accounts, developer accounts, and other assets that are often overlooked. You can also see if those apps are connected to other apps via OAuth grants, so you can minimize the chance of something breaking when an employee leaves the organization.
And, better yet, with Nudge Security, you can automate key steps of IT offboarding like suspending accounts, resetting passwords, revoking OAuth grants and more. And you’ll start with a full inventory of every account ever created for the departing employee so you can ensure all access is revoked.
Try Nudge Security for free
Our mission at Nudge Security is to help IT and security professionals everywhere regain control over SaaS security and governance while minimizing manual work for themselves and friction for end users. Start a free 14-day trial now to see what it can do for you.