Microsoft on Tuesday addressed a quartet of security flaws as part of its Patch Tuesday updates that could be abused by adversaries to target Azure cloud customers and elevate privileges as well as allow for remote takeover of vulnerable systems.
The list of flaws, collectively called OMIGOD by researchers from Wiz, affect a little-known software agent called Open Management Infrastructure that's automatically deployed in many Azure services -
- CVE-2021-38647 (CVSS score: 9.8) - Open Management Infrastructure Remote Code Execution Vulnerability
- CVE-2021-38648 (CVSS score: 7.8) - Open Management Infrastructure Elevation of Privilege Vulnerability
- CVE-2021-38645 (CVSS score: 7.8) - Open Management Infrastructure Elevation of Privilege Vulnerability
- CVE-2021-38649 (CVSS score: 7.0) - Open Management Infrastructure Elevation of Privilege Vulnerability
Open Management Infrastructure (OMI) is an open-source analogous equivalent of Windows Management Infrastructure (WMI) but designed for Linux and UNIX systems such as CentOS, Debian, Oracle Linux, Red Hat Enterprise Linux Server, SUSE Linux, and Ubuntu that allows for monitoring, inventory management, and syncing configurations across IT environments.
Azure customers on Linux machines, including users of Azure Automation, Azure Automatic Update, Azure Operations Management Suite (OMS), Azure Log Analytics, Azure Configuration Management, and Azure Diagnostics, are at risk of potential exploitation.
"When users enable any of these popular services, OMI is silently installed on their virtual machine, running at the highest privileges possible," Wiz security researcher Nir Ohfeld said. "This happens without customers' explicit consent or knowledge. Users simply click agree to log collection during set-up and they have unknowingly opted in."
"In addition to Azure cloud customers, other Microsoft customers are affected since OMI can be independently installed on any Linux machine and is frequently used on-premise," Ohfeld added.
Since the OMI agent runs as root with the highest privileges, the aforementioned vulnerabilities could be abused by external actors or low-privileged users to remotely execute code on target machines and escalate privileges, thereby enabling the threat actors to take advantage of the elevated permissions to mount sophisticated attacks.
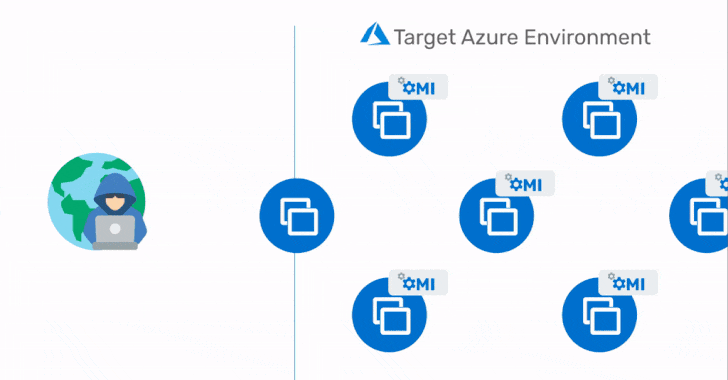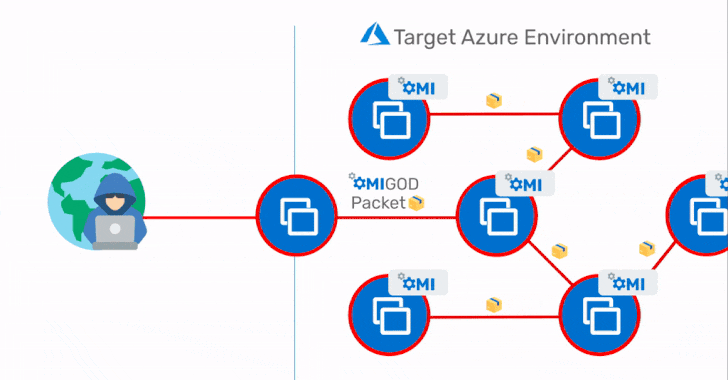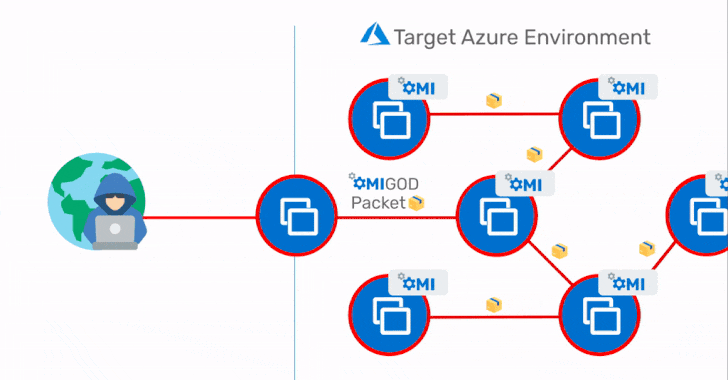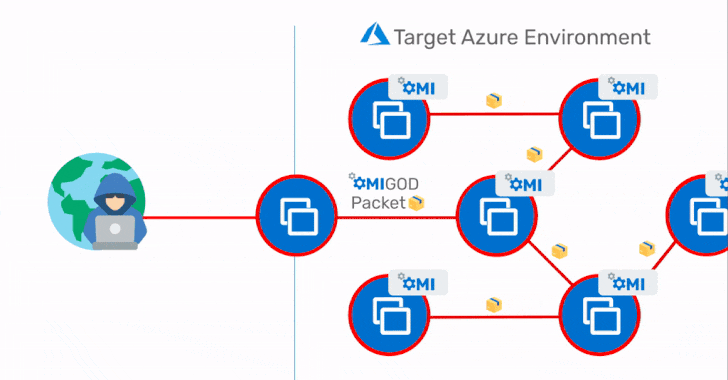
The most critical of the four flaws is a remote code execution flaw arising out of an internet-exposed HTTPS port like 5986, 5985, or 1270, allowing attackers to obtain initial access to a target Azure environment and subsequently move laterally within the network.
"This is a textbook RCE vulnerability that you would expect to see in the 90's – it's highly unusual to have one crop up in 2021 that can expose millions of endpoints," Ohfeld said. "With a single packet, an attacker can become root on a remote machine by simply removing the authentication header. It's that simple."
"OMI is just one example of a 'secret' software agent that's pre-installed and silently deployed in cloud environments. It's important to note that these agents exist not just in Azure but in [Amazon Web Services] and [Google Cloud Platform] as well."
Update: Microsoft on Thursday published additional guidance for the OMIGOD vulnerabilities, urging customers to apply the updates manually as and when they become available per the schedule outlined here. The security issues impact all versions of OMI below 1.6.8-1.
"Several Azure Virtual Machine (VM) management extensions use [the OMI] framework to orchestrate configuration management and log collection on Linux VMs," Microsoft Security Response Center said in a bulletin. "The remote code execution vulnerability only impacts customers using a Linux management solution (on-premises SCOM or Azure Automation State Configuration or Azure Desired State Configuration extension) that enables remote OMI management."
The development comes as Bad Packets reported mass scanning of Azure Linux-based servers vulnerable to the remote code execution flaw in an attempt to hijack vulnerable systems and mount further attacks, which, in turn, have been fueled by the public release of a proof-of-concept (PoC) exploit.