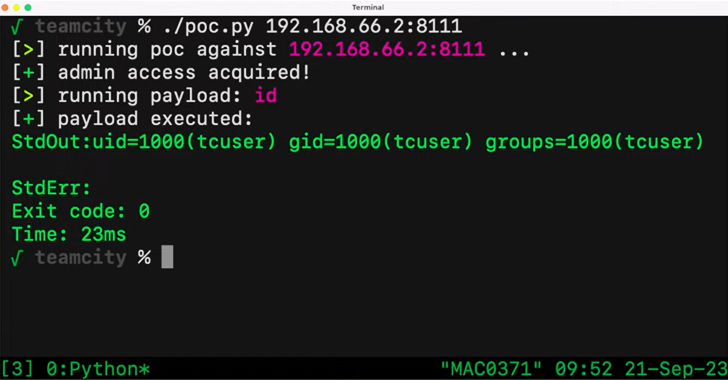
A critical security vulnerability in the JetBrains TeamCity continuous integration and continuous deployment (CI/CD) software could be exploited by unauthenticated attackers to achieve remote code execution on affected systems.
The flaw, tracked as CVE-2023-42793, carries a CVSS score of 9.8 and has been addressed in TeamCity version 2023.05.4 following responsible disclosure on September 6, 2023.
"Attackers could leverage this access to steal source code, service secrets, and private keys, take control over attached build agents, and poison build artifacts," Sonar security researcher Stefan Schiller said in a report last week.
Successful exploitation of the bug could also permit threat actors to access the build pipelines and inject arbitrary code, leading to an integrity breach and supply chain compromise.
It's worth noting that the shortcoming only affects on-premise versions of the JetBrains software. The TeamCity Cloud version has already been updated with the latest fixes.
Additional details of the bug have been withheld due to the fact that it's trivial to exploit, with Sonar noting that it's likely to be weaponized in the wild by threat actors.
JetBrains, in an independent advisory, has recommended users to upgrade as soon as possible. It has also released a security patch plugin for TeamCity versions 8.0 and above to specifically address the flaw.
The disclosure comes as two high-severity flaws have been disclosed in the Atos Unify OpenScape products that allow a low-privileged attacker to execute arbitrary operating systems commands as root user (CVE-2023-36618) as well as an unauthenticated attacker to access and execute various configuration scripts (CVE-2023-36619).
The flaws were patched by Atos in July 2023.
Over the past few weeks, Sonar has also published details about critical cross-site scripting (XSS) vulnerabilities affecting encrypted email solutions, including Proton Mail, Skiff, and Tutanota, that could have been weaponized to steal emails and impersonate victims.
Active Exploitation of JetBrains TeamCity Flaw Detected
Threat actors such as ransomware groups have begun to actively weaponize a recently disclosed critical bug in JetBrains TeamCity that could result in remote code execution, according to reports from GreyNoise, PRODAFT, and the Shadowserver Foundation.
Malicious exploitation attempts have been detected from 57 different IP addresses in Germany, the U.S., the Netherlands, Romania, and Denmark, as of October 2, 2023. More than 1,200 unique servers are estimated to be susceptible to the flaw.