A security vulnerability has been found affecting several versions of ThroughTek Kalay P2P Software Development Kit (SDK), which could be abused by a remote attacker to take control of an affected device and potentially lead to remote code execution.
Tracked as CVE-2021-28372 (CVSS score: 9.6) and discovered by FireEye Mandiant in late 2020, the weakness concerns an improper access control flaw in ThroughTek point-to-point (P2P) products, successful exploitation of which could result in the "ability to listen to live audio, watch real time video data, and compromise device credentials for further attacks based on exposed device functionality."
"Successful exploitation of this vulnerability could permit remote code execution and unauthorized access to sensitive information, such as to camera audio/video feeds," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) noted in an advisory.
There are believed to be 83 million active devices on the Kalay platform. The following versions of Kalay P2P SDK are impacted -
- Versions 3.1.5 and prior
- SDK versions with the nossl tag
- Device firmware that does not use AuthKey for IOTC connection
- Device firmware using the AVAPI module without enabling DTLS mechanism
- Device firmware using P2PTunnel or RDT module
The Taiwanese company's Kalay platform is a P2P technology that allows IP cameras, light cameras, baby monitors, and other internet-enabled video surveillance products to handle secure transmission of large audio and video files at low latency. This is made possible through the SDK – an implementation of the Kalay protocol – that's integrated into mobile and desktop apps and networked IoT devices.
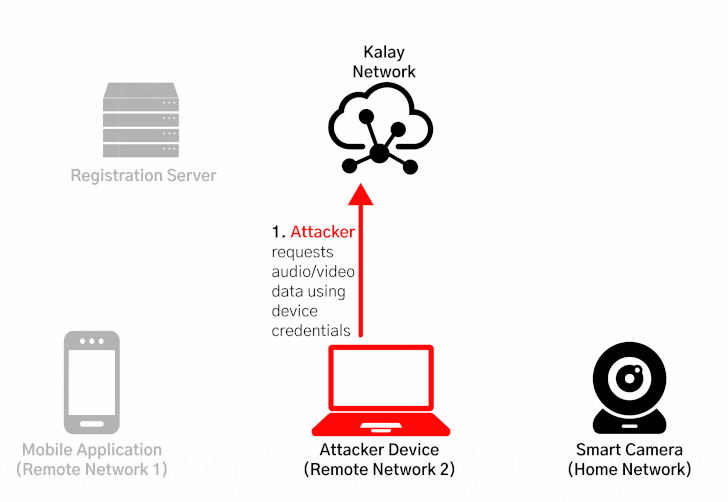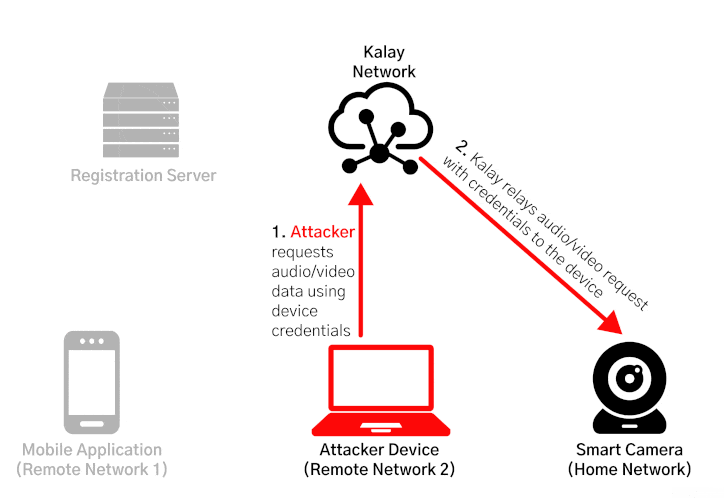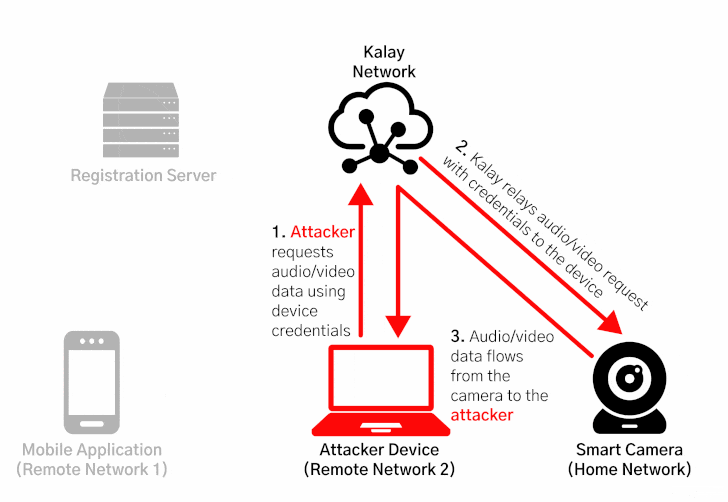
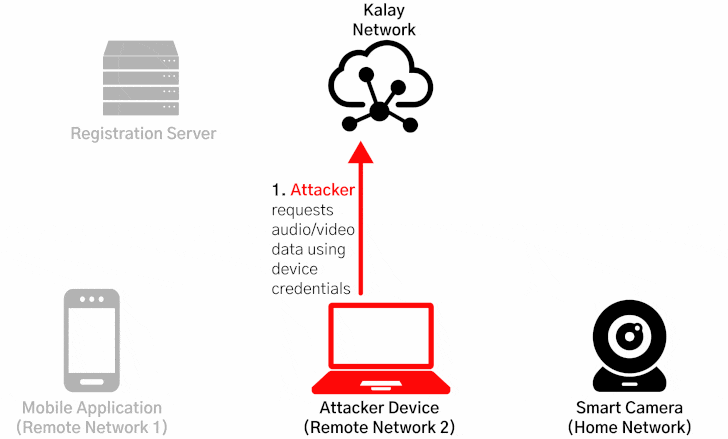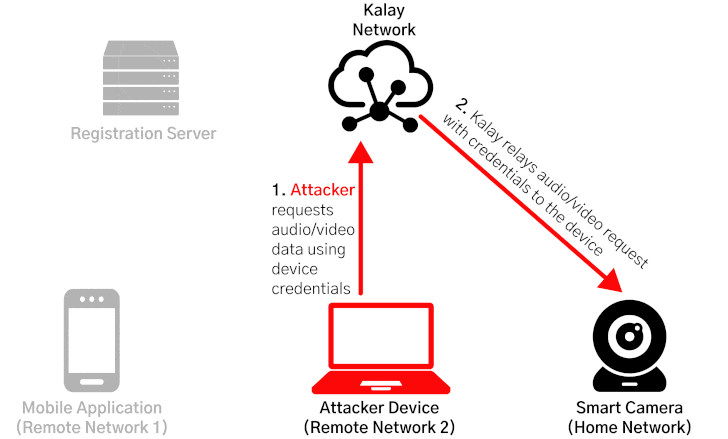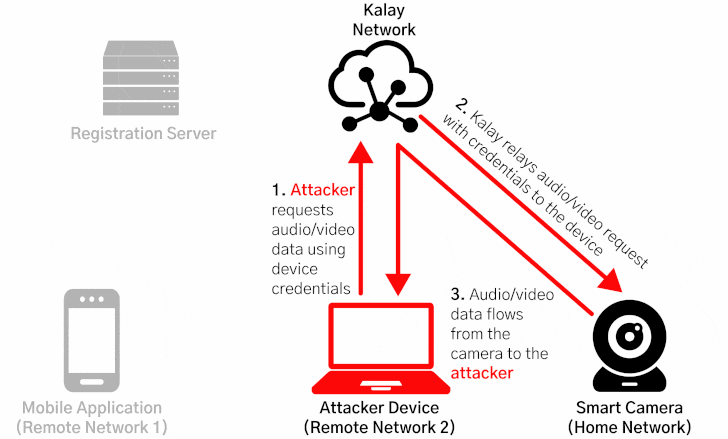
CVE-2021-28372 resides in the registration process between the devices and their mobile applications, specifically concerning how they access and join the Kalay network, enabling attackers to spoof a victim device's identifier (called UID) to maliciously register a device on the network with the same UID, causing the registration servers to overwrite the existing device and route the connections to be mistakenly routed to the rogue device.
"Once an attacker has maliciously registered a UID, any client connection attempts to access the victim UID will be directed to the attacker," the researchers said. "The attacker can then continue the connection process and obtain the authentication materials (a username and password) needed to access the device. With the compromised credentials, an attacker can use the Kalay network to remotely connect to the original device, access AV data, and execute RPC calls."
However, it's worth pointing out that an adversary would require "comprehensive knowledge" of the Kalay protocol, not to mention obtain the Kalay UIDs through social engineering or other vulnerabilities in APIs or services that could be taken advantage of to pull off the attacks.
To mitigate against any potential exploitation, it's recommended to upgrade the Kalay protocol to version 3.1.10 as well as enable DTLS and AuthKey to secure data in transit and add an additional layer of authentication during client connection.
The development marks the second time a similar vulnerability has been disclosed in ThroughTek's P2P SDK. In June 2021, CISA issued an alert warning of a critical flaw (CVE-2021-32934) that could be leveraged to access the camera audio and video feeds through improper means.