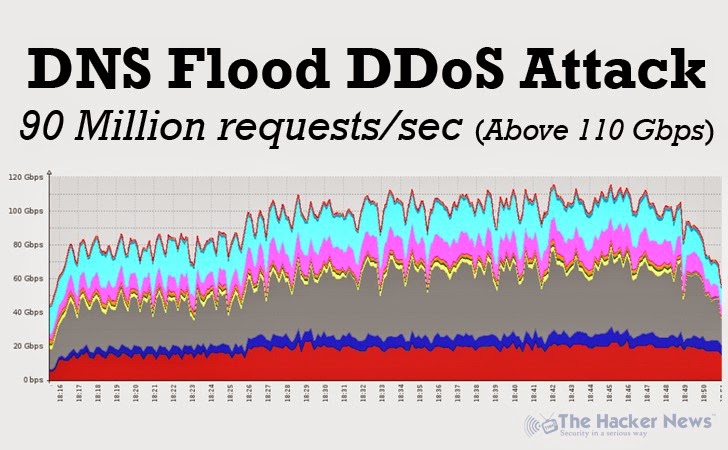
Hackers are leveraging large number of compromised machines (a botnet network) to carry out massive DNS Flood DDoS attack against a large Video Gaming Industry website, peaking above 110 Gbps.
A US based security solutions provider Incapsula, is protecting a famous Video Gaming website from this high bandwidth DDoS attack from last 48 Hours and according to them, the attack is still continuing. Incapsula has not yet disclosed the name of the video gaming company.
"The attack is still going on - that over 48 hours by now, from what I see it ain't gonna stop anytime soon," Incapsula spokesperson wrote in an e-mail to The Hacker News.
DDoS AT 90 MILLION PACKETS/SECOND
The researchers at the security firm noticed a surge of massive DNS Flood DDoS attack on one of its clients, peaking at approximately 90 Mpps (Million Packets Per Second), which is really a very very big number. Majority number of attacking IP addresses belong to China and India. "Good reason to think many are spoofed." Incapsula told THN.
The hackers used a more evil DDoS practice, the DNS flood attack, which is completely different and more responsive from the previously most commonly used DNS amplification attack, both in their methods of execution and in the type of grief they aim to deliver.
On one side, where DNS amplification attack is an asymmetrical DDoS attack, in which an attacker set the source address to that of the targeted victim by using spoofed Internet Protocol (IP) of the target, which means the target receives the replies from all the DNS servers that are used, making it the recipient of much larger DNS responses.
DNS FLOOD WITHOUT AMPLIFICATION
On the other side, DNS floods attacks are symmetrical DDoS attacks that works by sending thousands of rapid valid DNS requests to the targeted server, thereby giving the server more traffic than it can handle resulting in slower and slower response times for legitimate requests.
DNS servers provide the roadmap to the Internet, and help clients find the servers they are looking for, but a DNS floods attempt to exhaust server-side assets (for e.g., memory or CPU) with the large number of UDP requests generated by the malicious scripts running on several compromised botnet machines. The packets sends per seconds are even larger in this case compare to DNS amplification attack.
Currently researchers at the DDoS protection service are mitigating with this attack with just one of their servers, that can process upto 170Gbps/100Mpps worth of traffic at an inline rate.
Until now, we have seen 50-60Gbps DNS Flood DDoS attack without amplification, but reaching above 110Gbps seems that hackers are making their comeback in really a very big way.
As we all have seen that DDoS trend is changing and to perform massive DDoS attacks, hacker are using every tantrum by leveraging the weakness of system applications to compromise them in order to boost the size of their botnet network.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.