Phoenix Exploit’s Kit 2.8 mini version
Back in April of this year, we reported the leak of Phoenix Exploit Kit 2.5. The version currently in circulation is 2.8, and despite its lower activity for the last half of this year, it remains one of the preferred exploit packs used by cyber-criminals.
In comparison to the Black Hole Exploit Pack, the PEK has a similar licensing model. The last version released offered an “alternative” to purchasing the exploit pack. This “alternative” is the Phoenix Exploit’s Kit 2.8 mini.
The current licensing model consists of the following:
The mini version does not change the characteristics of the Exploit Pack, at least in regards to its graphical interface and functionality in relation to previous versions. Each section has the same type of display and statistical information, which is provided in a minimalistic yet concise manner. Although trivial, this is one of the main reasons for the adoption of Phoenix by cyber-criminals. The ability to easily locate information and merge the functionality of this Exploit Pack with a Malware Kit, such as SpyEye or ZeuS, increases their level of success and attack strategies.
The main difference between the full version and the mini version is that the mini version is subject to a domain under the simple mode, while the full version allows multitasking.
There isn’t much new about the Exploit Pack. The code has been optimized to increase the success rate of exploitation and the exploit for Java Runtime Environment to Trusted has been added.
Also removed were the following exploits pre-compiled in version 2.7:
Although it’s basically the same exploits (similar in all cases, including those incorporating other Exploit Packs in the wild), the author's optimized for each version. In this case, it includes the following exploits:
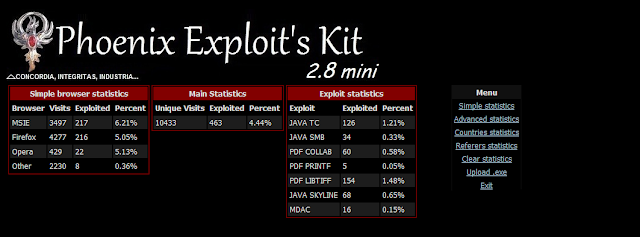
Despite the optimization of the components for each version, it is interesting that chain optimization and updating MDAC exploits remains the most prevalent, not only in this Exploit Pack but in any of the existing Exploit Packs. What is the reason? It comes down to a lack of experience by the users (application, customers around the basic procedures update) that transforms them into a potential target and highly susceptible through this old, but effective vulnerability.
[Source]
Back in April of this year, we reported the leak of Phoenix Exploit Kit 2.5. The version currently in circulation is 2.8, and despite its lower activity for the last half of this year, it remains one of the preferred exploit packs used by cyber-criminals.
In comparison to the Black Hole Exploit Pack, the PEK has a similar licensing model. The last version released offered an “alternative” to purchasing the exploit pack. This “alternative” is the Phoenix Exploit’s Kit 2.8 mini.
The current licensing model consists of the following:
· Simple Domain (Closed) – USD $2,200.00
· Multithreaded Domain (Closed) – USD $2,700.00
· Extra-Encryption Service (ReFUDing) – USD $40.00
The mini version does not change the characteristics of the Exploit Pack, at least in regards to its graphical interface and functionality in relation to previous versions. Each section has the same type of display and statistical information, which is provided in a minimalistic yet concise manner. Although trivial, this is one of the main reasons for the adoption of Phoenix by cyber-criminals. The ability to easily locate information and merge the functionality of this Exploit Pack with a Malware Kit, such as SpyEye or ZeuS, increases their level of success and attack strategies.
The main difference between the full version and the mini version is that the mini version is subject to a domain under the simple mode, while the full version allows multitasking.
There isn’t much new about the Exploit Pack. The code has been optimized to increase the success rate of exploitation and the exploit for Java Runtime Environment to Trusted has been added.
Also removed were the following exploits pre-compiled in version 2.7:
· Windows Help and Support Center Protocol Handler Vulnerability – CVE-2010-1885
· Integer overflow in the AVM2 abcFile parser in Adobe Flash Player – CVE-2009-1869
· Integer overflow in Adobe Flash Player 9 – CVE-2007-0071
· IEPeers Remote Code Execution – CVE-2009-0806
· Internet Explorer Recursive CSS Import Vulnerability – CVE-2010-3971
Although it’s basically the same exploits (similar in all cases, including those incorporating other Exploit Packs in the wild), the author's optimized for each version. In this case, it includes the following exploits:
· Microsoft Data Access Components (MDAC) - CVE-2006-0003
· Adobe Reader Javascript Printf Buffer Overflow - CVE-2008-2992
· Adobe Reader LibTiff - CVE-2010-0188
· Adobe Reader Collab GetIcon - CVE-2009-0927
· Java SMB - CVE-2010-0746
· Java Runtime Environment Trusted - CVE-2010-0840
· Java Skyline Plug-in component in Oracle Java SE and Java for Business 6 - CVE-2010-3552
· Java Deployment Toolkit Component - CVE-2010-0886
Despite the optimization of the components for each version, it is interesting that chain optimization and updating MDAC exploits remains the most prevalent, not only in this Exploit Pack but in any of the existing Exploit Packs. What is the reason? It comes down to a lack of experience by the users (application, customers around the basic procedures update) that transforms them into a potential target and highly susceptible through this old, but effective vulnerability.
[Source]
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.