Apache Patch released for Reverse proxy Bypass Vulnerability
Security experts at Context have discovered a hole in the Apache web server that allows remote attackers to access internal servers. Security experts are warning firms running the Apache web server to keep up to date with the latest patches after the Apache Software Foundation issued a security advisory to all customers highlighting a new vulnerability. The weakness in 1.3 and all 2.x versions of the Apache HTTP Server can be exploited only under certain conditions.
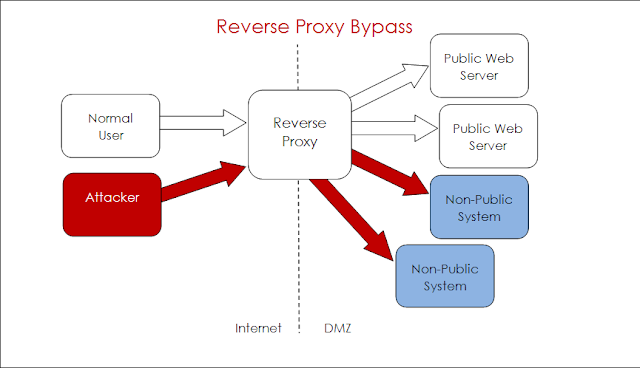
Reverse proxies are used to route external HTTP and HTTPS web requests to one of several internal web servers to access data and resources. Typical applications include load balancing, separating static from dynamic content, or to present a single interface to a number of different web servers at different paths.
Context explained that the attack is based on an Apache web server using the mod_rewrite proxy function, and uses a common hacking tool to change the request to access DMZ systems."We can access any internal/DMZ system which the proxy can access including administration interfaces on firewalls, routers, web servers, databases etc," the firm said."Context has had plenty of success with this attack where credentials are weak on the internal systems allowing for full network compromise e.g. uploading Trojan WAR files on to JBoss servers."
Apache issued a patch for those who compile their own installations of the webserver. It wouldn't be surprising to see Linux distributions release their own security updates in the next few days. Apache's advisory also contains suggestions for writing proxy rules that prevent the attack from working. Adding a simple forward slash to certain configurations, for example, will go a long way to protecting sensitive systems. The line is "RewriteRule (.*)\.(jpg|gif|png)" could expose internal servers, while the line "RewriteRule /(.*)\.(jpg|gif|png)" (note the extra "/") will ensure they remain protected.
The best way to prevent this type of attack is to apply the new Apache patch and run the latest version of the software, and to ensure that your reverse proxy rewrite rules can't be employed to access internal systems, according to Context.
Security experts at Context have discovered a hole in the Apache web server that allows remote attackers to access internal servers. Security experts are warning firms running the Apache web server to keep up to date with the latest patches after the Apache Software Foundation issued a security advisory to all customers highlighting a new vulnerability. The weakness in 1.3 and all 2.x versions of the Apache HTTP Server can be exploited only under certain conditions.
Reverse proxies are used to route external HTTP and HTTPS web requests to one of several internal web servers to access data and resources. Typical applications include load balancing, separating static from dynamic content, or to present a single interface to a number of different web servers at different paths.
Context explained that the attack is based on an Apache web server using the mod_rewrite proxy function, and uses a common hacking tool to change the request to access DMZ systems."We can access any internal/DMZ system which the proxy can access including administration interfaces on firewalls, routers, web servers, databases etc," the firm said."Context has had plenty of success with this attack where credentials are weak on the internal systems allowing for full network compromise e.g. uploading Trojan WAR files on to JBoss servers."
Apache issued a patch for those who compile their own installations of the webserver. It wouldn't be surprising to see Linux distributions release their own security updates in the next few days. Apache's advisory also contains suggestions for writing proxy rules that prevent the attack from working. Adding a simple forward slash to certain configurations, for example, will go a long way to protecting sensitive systems. The line is "RewriteRule (.*)\.(jpg|gif|png)" could expose internal servers, while the line "RewriteRule /(.*)\.(jpg|gif|png)" (note the extra "/") will ensure they remain protected.
The best way to prevent this type of attack is to apply the new Apache patch and run the latest version of the software, and to ensure that your reverse proxy rewrite rules can't be employed to access internal systems, according to Context.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.