The Zemra DDoS Bot is currently sold in various forums for about 100 € and detected by Symantec as Backdoor.Zemra. Zemra first appeared on underground forums in May 2012.
This crimeware pack is similar to other crime packs, such as Zeus and SpyEye, in that is has a command-and-control panel hosted on a remote server.
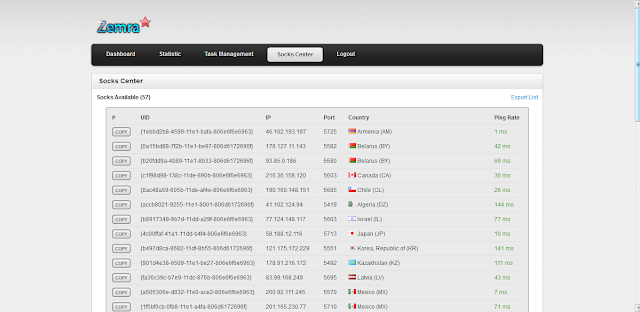
Zemra uses a simple panel with an overview of all statistics is needed.With the help of two graphs can be seen operating machinery and the region location.In addition, statistics on online and for more information. You have a chance to see everything online Socks5 and export them to the list.Traffic is encrypted and protected using the algorithm AES, each client communicates with a unique generated key.
Note : In "Tools Yard" we have Posted Zemra Source Code, Only for Educational Purpose.
Zemra uses a simple panel with an overview of all statistics is needed.With the help of two graphs can be seen operating machinery and the region location.In addition, statistics on online and for more information. You have a chance to see everything online Socks5 and export them to the list.Traffic is encrypted and protected using the algorithm AES, each client communicates with a unique generated key.
Note : In "Tools Yard" we have Posted Zemra Source Code, Only for Educational Purpose.
A brief functional:
• Intuitive control panel
• DDos (HTTP / SYN Flood / UDP)
• Loader (Load and run).
• Cheat visits (visits to the page views).
• USB Spread (spread through flash drives)
• Socks5 (picks up socks proxy on the infected machine)
• Update (Updates the bot)
• [color = red] The process can not be completed because the He is critical.
• 256 Bit AES encryption of traffic from the bot to the server
• Anti-Debugger
• There is a choice of a particular country bots perform the job
After inspecting the source code, symantec identifies that two types of DDoS attacks that have been implemented into this bot: HTTP flood and SYN flood.
"To reduce the possibility of being infected by this Trojan, Symantec advises users to ensure that they are using the latest Symantec protection technologies with the latest antivirus definitions installed." Symantec suggest in a blog post.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.