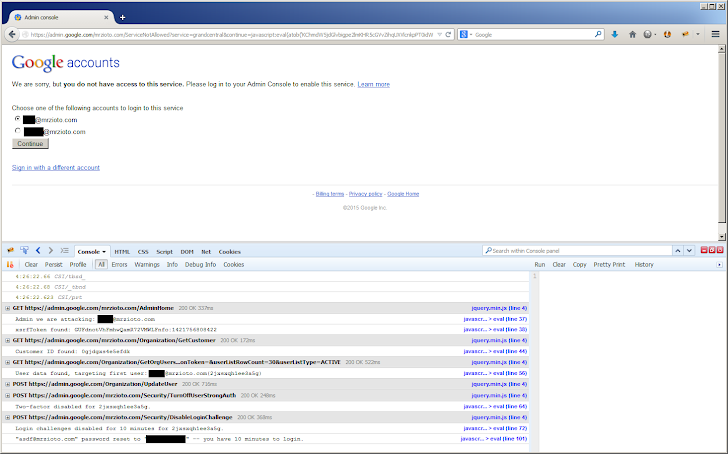
A critical cross-site scripting (XSS) vulnerability in the Google Apps administrator console allowed cyber criminals to force a Google Apps admins to execute just about any request on the https://admin.google.com/ domain.
The Google Apps admin console allows administrators to manage their organization's account. Administrators can use the console to add new users, configure permissions, manage security settings and enable Google services for your domain. The feature is primarily used by many businesses, especially those using Gmail as the e-mail service for their domain.
The XSS flaw allowed attackers to force the admin to do the following actions:
- Creating new users with "super admin" rights
- Disabling two-factor authentication (2FA) and other security measures from existing accounts or from multiple domains
- Modifying domain settings so that all incoming e-mails are redirected to addresses controlled by the attacker
- Hijack an account/email by resetting the password, disabling 2FA, and also removing login challenges temporarily for 10 minutes
This new zero-day vulnerability was discovered and privately reported by application security engineer Brett Buerhaus to Google on September 1 and the company fixed the flaw within 17 days. In exchange for the report, Google paid the researcher $5,000 as a reward under its bug bounty program.
According to the researcher, when users access a service that hasn't been configured for their domain, they are presented with a "ServiceNotAllowed" page. This page allows users to switch between accounts in order to log in to the service.
However, when one of the accounts was selected, a piece of JavaScript code was executed in an attempt to redirect the user's Web browser. JavaScript code could be supplied by the user in the "continue" request parameter of the URL, which allowed XSS attacks.
"The continue request parameter is fairly common request variable in the Google login flow," Buerhaus explained in a blog post published on Wednesday. "This is the only page that I could find that did not validate the URL passed into it. This allowed you to craft Cross-Site Scripting attacks by using "javascript:" as part of the URL and it would execute when the browser location is redirected."
Patching the vulnerability on the 17th day after reported to the company shows the search engine giant's concern to secure its software and users as well.
However, the recent vulnerability troubles visited Microsoft exposed one-after-one three serious zero-day vulnerabilities in Windows 7 and 8.1 operating systems, reported by Google's Project Zero team. Microsoft wasn't able to fix the security flaws in its software even after a three-month-long time period provided to the company.
However, the recent vulnerability troubles visited Microsoft exposed one-after-one three serious zero-day vulnerabilities in Windows 7 and 8.1 operating systems, reported by Google's Project Zero team. Microsoft wasn't able to fix the security flaws in its software even after a three-month-long time period provided to the company.
Found this article interesting? Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.