Simple Mail Transfer Protocol or SMTP has easily exploitable security loopholes. Email routing protocols were designed in a time when cryptographic technology was at a nascent stage (e.g., the de-facto protocol for email transfer, SMTP, is nearly 40 years old now), and therefore security was not an important consideration.
As a result, in most email systems encryption is still opportunistic, which implies that if the opposite connection does not support TLS, it gets rolled back to an unencrypted one delivering messages in plaintext.
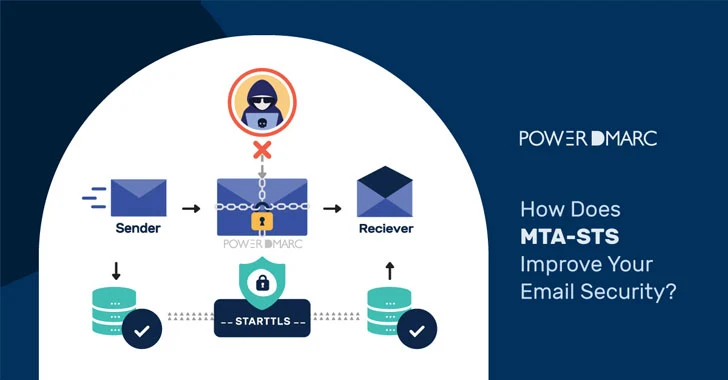
To mitigate SMTP security problems, MTA-STS (Mail Transfer Agent Strict Transport Security) is the recommended email authentication standard. It enforces TLS in order to allow MTAs to send emails securely. This means that it will only allow mail from MTAs that support TLS encryption, and it will only allow mail to go to MX hosts that support TLS encryption.
In case an encrypted connection cannot be negotiated between communicating SMTP servers, the email is not sent, instead of being sent over an unencrypted connection.
Analyzing the risks involved in transferring emails over an unencrypted SMTP connection
STARTTLS is a communication protocol extension to the SMTP email transfer protocol that allows both the communication partners to upgrade an unencrypted communication to encrypted communication. This backward-compatible security implementation was retrofitted into SMTP to ensure that all clients can connect with some level of encryption. When SMTP was first created in the 1980s, it didn't have any security measures to ensure the communication between mail servers was sent in an encrypted form—it just sent mail as plain text.
A known vulnerability in the protocol design of the SMTP can be exploited to downgrade a connection easily. Since SMTP was not designed to be encrypted, the upgrade for encrypted delivery is performed by sending an unencrypted STARTTLS command. This enables a Man-in-the-middle attacker to tamper with the STARTTLS command, thereby downgrading the TLS-encrypted connection to an unencrypted one. This forces the email client to fall back to sending information in plaintext. The attacker can then easily access and eavesdrop on the decrypted information.
Cyber Eavesdropping attacks like MITM can jeopardize sensitive information exchanged between officials of an organization, leading to the leakage of company databases and login credentials.
How to Ensure TLS Encryption with MTA-STS?
MTA-STS makes TLS encryption mandatory in SMTP, which ensures that messages are not sent over an unsecured connection, or delivered in plaintext. This in turn keeps Man-in-the-middle and DNS spoofing attacks at bay by stopping attackers from intercepting email communications.
PowerDMARC's hosted MTA-STS services help eliminate the complications that come with adopting the protocol, by making the overall process easy for domain owners.
Our hosted MTA-STS provides domain owners with the following benefits:
- We host and manage the policy files and certificates on your behalf
- Adopting the protocol is as easy as publishing a few DNS CNAME records, making it effortless and speedy
- A dedicated dashboard to manage and modify the protocol configurations that enable you to make changes to your MTA-STS record without having to access your DNS
- PowerDMARC's hosted MTA-STS services meet the RFC compliance requirements as well as the current TLS standards
What concerns domain owners after implementing MTA-STS is how to get alerted during situations where an encrypted connection cannot be negotiated and messages fail to get delivered. However, keeping this issue in mind experts curated SMTP TLS reporting, a mechanism that notifies you of delivery issues.
How to View and Manage Your TLS Reports?
TLS-RPT allows you to get notified of email delivery failure on TLS encrypted channels; it analyzes and reports all possible issues within those channels, allowing you to react to a TLS issue and deliver a message back without any delay. It is an excellent addition to MTA-STS as it addresses the concern pertaining to emails getting lost during transfer.
PowerDMARC's hosted TLS-RPT services:
- Gives you access to a dedicated dashboard that automatically parses your TLS reports (originally sent in JSON format), to make them simple and human-readable
- TLS-RPT data is organized into tables, with actionable buttons and icons for ease of use and navigation
- Furthermore, your reports are assorted into two separate viewing formats: per sending source and per result, for better visibility and clarity, and an enhanced user experience.
PowerDMARC helps you deploy and manage email authentication solutions like DMARC, SPF, DKIM, BIMI, MTA-STS, and TLS-RPT, under a single roof without having to deploy them separately for your domain!
To avail the benefits of email authentication at your organization, and combat the risk of phishing, spoofing, ransomware, and MITM attacks, sign up for a free DMARC Analyzer today!