Nearly two years back, we warned users about publicly accessible MongoDB instances – almost 600 Terabytes (TB) – over the Internet which require no authentication, potentially leaving websites and servers at risk of hacking.
These MongoDB instances weren't exposed due to any flaw in its software, but due to a misconfiguration (bad security practice) that let any remote attacker access MongoDB databases without using any special hacking tool.
MongoDB later resolved the issue in the next version of its software by setting unrestricted remote access by default in the configuration, thousands of site administrators have not updated their servers yet.
But trust me, they'll now regret this!
A Hacker is now hijacking and wiping out unsecured MongoDB databases, but keeping a copy of those databases for asking administrators a ransom of 0.2 Bitcoins (nearly US$211) to return the lost data. So, admins without backups are left in a bind.
In fact, the rising price of Bitcoin even hints at some of its troubles. At the time od writing, 1 Bitcoin = USD1063.93.
Security researcher and co-founder of the GDI Foundation Victor Gevers (@0xDUDE) discovered the attacks and notified exposed non-password-protected MongoDB installations to owners via Twitter.
Gevers identified nearly 200 instances of a MongoDB installation that's been erased and held for ransom, while this number reached approximately 2,000 databases as of 4:00 p.m, as reported by John Matherly, the Founder of Shodan, where many exposed MongoDB databases can be found.
These attacks have been going on for over a week, targeting servers all over the world. It is believed that instead of encrypting the data, the attacker who goes by the name "harak1r1," ran a script that replaced the content of the database with the attacker's ransom note.
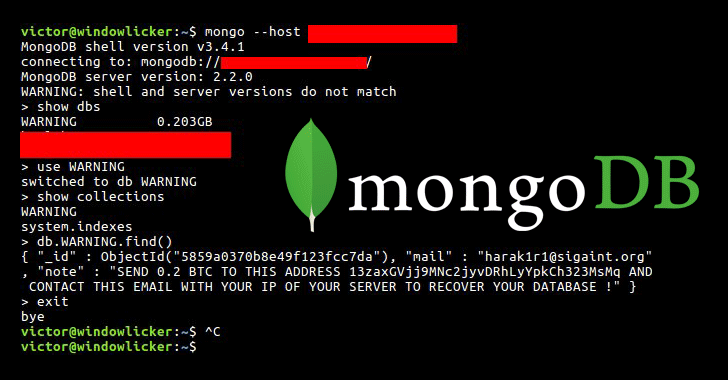
While accessing one of the open servers, Gevers found that in place of the database content, there is only one table, named "WARNING," which reads:
It appears that around 16 organizations so far have paid the ransom to the attacker.
Matherly has been warning of the dangers of exposed MongoDB installations since 2015, allowing an attacker to remotely access the databases over the Internet without the need of any form of authentication.
Matherly said the majority of publicly exposed 30,000 MongoDB instances run on cloud servers such as Amazon, Digital Ocean, Linode, and Internet service and hosting provider OVH and do so without authentication, making cloud services buggier than datacenter hosting.
These MongoDB instances weren't exposed due to any flaw in its software, but due to a misconfiguration (bad security practice) that let any remote attacker access MongoDB databases without using any special hacking tool.
MongoDB later resolved the issue in the next version of its software by setting unrestricted remote access by default in the configuration, thousands of site administrators have not updated their servers yet.
But trust me, they'll now regret this!
A Hacker is now hijacking and wiping out unsecured MongoDB databases, but keeping a copy of those databases for asking administrators a ransom of 0.2 Bitcoins (nearly US$211) to return the lost data. So, admins without backups are left in a bind.
In fact, the rising price of Bitcoin even hints at some of its troubles. At the time od writing, 1 Bitcoin = USD1063.93.
Security researcher and co-founder of the GDI Foundation Victor Gevers (@0xDUDE) discovered the attacks and notified exposed non-password-protected MongoDB installations to owners via Twitter.
Gevers identified nearly 200 instances of a MongoDB installation that's been erased and held for ransom, while this number reached approximately 2,000 databases as of 4:00 p.m, as reported by John Matherly, the Founder of Shodan, where many exposed MongoDB databases can be found.
These attacks have been going on for over a week, targeting servers all over the world. It is believed that instead of encrypting the data, the attacker who goes by the name "harak1r1," ran a script that replaced the content of the database with the attacker's ransom note.
While accessing one of the open servers, Gevers found that in place of the database content, there is only one table, named "WARNING," which reads:
"SEND 0.2 BTC TO THIS ADDRESS 13zaxGVjj9MNc2jyvDRhLyYpkCh323MsMq AND CONTACT THIS EMAIL WITH YOUR IP OF YOUR SERVER TO RECOVER YOUR DATABASE !"
16 Victims Already Paid the Ransom
It appears that around 16 organizations so far have paid the ransom to the attacker.
Matherly has been warning of the dangers of exposed MongoDB installations since 2015, allowing an attacker to remotely access the databases over the Internet without the need of any form of authentication.
Matherly said the majority of publicly exposed 30,000 MongoDB instances run on cloud servers such as Amazon, Digital Ocean, Linode, and Internet service and hosting provider OVH and do so without authentication, making cloud services buggier than datacenter hosting.
How to Know if You've Been Hacked?
- Check the MongoDB accounts to see if no one added a secret (admin) user.
- Check the GridFS to look if someone stored any files there.
- Check the log files to see who accessed the MongoDB.
How to Protect Yourself?
- Enable authentication that provides you 'Defense in depth' if your network is compromised. Edit your MongoDB configuration file — auth = true.
- Use firewalls — Disable remote access to the MongoDB, if possible. Admins are advised to use firewalls to protect the MongoDB installations by blocking access to port no. 27017.
- Configure Bind_ip — Limit access to the server by binding local IP addresses.
- Upgrade — Administrators are strongly recommended to upgrade their software to the latest release.