Socially engineered SMS messages are being used to install malware on Android devices as part of a widespread phishing campaign that impersonates the Iranian government and social security services to make away with credit card details and steal funds from victims' bank accounts.
Unlike other variants of banking malware that bank of overlay attacks to capture sensitive data without the knowledge of the victim, the financially motivated operation uncovered by Check Point Research is designed to trick the targets into handing over their credit card information by sending them a legitimate-looking SMS message that contains a link, which, when clicked, downloads a malware-laced app onto their devices.
"The malicious application not only collects the victim's credit card numbers, but also gains access to their 2FA authentication SMS, and turn[s] the victim's device into a bot capable of spreading similar phishing SMS to other potential victims," Check Point researcher Shmuel Cohen said in a new report published Wednesday.
The cybersecurity firm said it uncovered several hundred different phishing Android applications that masqueraded as device tracking apps, Iranian banks, dating and shopping sites, cryptocurrency exchanges, and government-related services, with these botnets sold as a "ready-to-use mobile campaign kit" on Telegram channels for anywhere between $50 to $150.
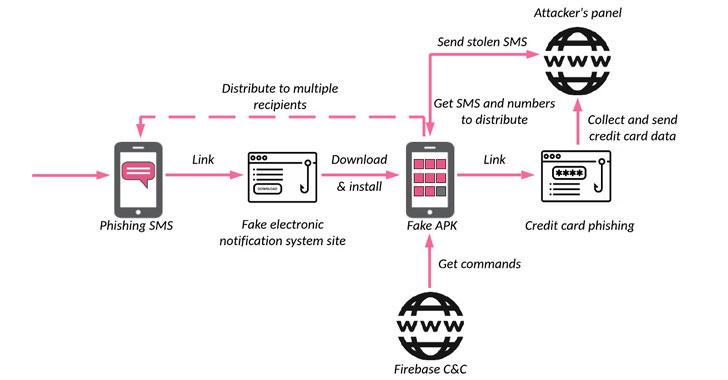
The smishing botnet's infection chain commences with a fake notification from the Iranian Judiciary urging users to review a supposed complaint filed against the recipients of the message. The link to the complaint directs the victims to what ostensibly looks like a government website, where they are asked to enter their personal information (e.g., name, phone number, etc.) and download an Android APK file.
Once installed, the rogue application not only requests for invasive permissions to perform activities that are not generally associated with such government apps, it also presents a fake login screen that mimics Sana, the country's electronic judicial notice system, and prompts the victim that they need to pay a $1 fee to proceed further.
Users opting to do so are then redirected to a fake payment page that collects the credit card information entered, while the installed app functions as a stealthy backdoor to surreptitiously steal one-time passcodes sent by the credit card company and facilitate additional theft.
Furthermore, the malware comes with a wealth of capabilities that allow it to exfiltrate all SMS messages received by a device to an attacker-controlled server, hide its icon from the home screen to thwart attempts to remove the app, deploy additional payloads, and acquire worm-like powers to expand its attack surface and spread custom smishing messages to a list of phone numbers retrieved from the server.
"This allows the actors to distribute phishing messages from the phone numbers of typical users instead of from a centralized place and not be limited to a small set of phone numbers that could be easily blocked," Cohen explained. "This means that technically, there are no 'malicious' numbers that can be blocked by the telecommunication companies or traced back to the attacker."
Making matters worse, the attackers behind the operation have been found to follow poor operational security (OPSEC), thereby making it possible for any third party to freely access the phone numbers, contacts, SMS messages, and the list of all the online bots hosted on their servers.
"Stealing 2FA dynamic codes allows the actors to slowly but steadily withdraw significant amounts of money from the victims' accounts, even in cases when due to the bank limitations each distinct operation might garner only tens of dollars," Cohen noted. "Together with the easy adoption of the 'botnet as a service' business model, it should come as no surprise that the number of such applications for Android and the number of people selling them is growing."